“Reduce false positives by 60% and detect threats 3x faster with actionable intelligence.”
Replacing Multiple-Point Solution Using Scalable Threat Detection for:




Supported Environments

Time saved with the deployment of ion's SIEM

Risk Reduced across multiple clouds

Time Saved in Threat Investigation

Efficiency improved for security operations team.
Cloud-Native SIEM is an integral part of cloud security operations that eliminates the limitations of legacy systems. Unlike traditional SIEMs constrained by hardware and manual processes, it delivers elastic scalability to handle unpredictable log volumes effortlessly.
Native integrations with AWS, Azure, OCI, and GCP ensure seamless visibility across hybrid environments, while AI-driven analytics uncover hidden threats with precision.
By incorporating ion’s SIEM, you can reduce infrastructure costs and maintenance burdens, while automatically staying updated with the latest threat intelligence. Most critically, we transform raw data into actionable insights—correlating threats across global networks to stop breaches before they escalate.

Automatically ranks threats by potential impact, ensuring critical risks get immediate attention.
Enhances alerts with environmental data (e.g., asset value, vulnerability) to focus on real threats.
Detects insider threats & compromised accounts by analysing deviations from normal activity patterns.

Auto-scales security workloads, reducing cost while maintaining threat detection across multiple clouds.
Centralizes security data with schema-on-read flexibility, enabling long-term analysis and threat hunting at scale.
Modern enterprises demand a SIEM solution engineered for the scale and complexity of today’s threat landscape—one that eliminates blind spots while maintaining performance under extreme data volumes. Our most advanced platforms combine massive ingestion capacity with intelligent processing to transform raw telemetry into actionable security insights, all while ensuring compliance across diverse infrastructure.
Pre-Built Log Parsers
Events Per Second Sustained

Correlation
Rules
Product
Integration

Compliance Frameworks
Third-Party Data Sources
Cloud attacks can unfold in under 10 minutes, but mature teams achieve <5-second alerting and <4-minute investigations with AI-driven SIEM.
Sysdig
Cy5’s SIEM solution focuses far beyond simple log collection—it delivers an intelligent, augmented defense system that turns raw data into decisive action. By combining lightning-fast search capabilities with threat correlation, security teams can cut through the noise to focus on genuine risks.
Real-time case management streamlines investigations, while remediation workflows eliminate manual bottlenecks. With built-in threat intelligence and dynamic dashboards, every alert is enriched with context—prioritizing what matters and proving compliance at a glance. This isn’t just monitoring; it’s proactive cyber defense that learns, adapts, and acts at machine speed.
Cy5’s SIEM platform delivers end-to-end operational intelligence by transforming raw data into actionable security outcomes. With frictionless onboarding and seamless log ingestion, it simplifies data collection and organization while ensuring system health. The platform’s cloud-scale analysis engine enables high-performance search, advanced threat correlation, and real-time intelligence.
Security teams benefit from streamlined workflows, integrated case management, and external system compatibility—empowering faster, smarter responses.
Cy5’s SIEM culminates in trusted, outcome-driven insights through robust reporting and dashboards, making it a powerful solution for organizations seeking certified security results and proactive protection from every data point.

Cy5’s SIEM simplifies security data onboarding: Automatically collect logs from any source, transform raw data into analysis-ready insights with smart normalization, and monitor pipeline health—eliminating manual work while ensuring complete data integrity for faster threat detection.
In Cy5’s SIEM, you can ingest logs from 1,200+ cloud, SaaS, and on-prem sources in minutes—no parsing, no plugins.
Cy5’s SIEM utilizes Grok-based parsing that enriches and normalizes raw logs into analysis-ready formats—eliminating manual prep work.
Cy5’s SIEM ensures pipeline diagnostics ensure 100% log integrity—get alerts for gaps before data loss occurs.
Cy5’s SIEM transforms raw data into decisive intelligence. Our next-gen engine detects hidden threats through lightning-fast investigations, connects attack patterns across silos, and enriches findings with live global intelligence—turning complex signals into actionable defense strategies.
Cy5’s SIEM can perform millisecond searches across petabytes of logs—uncover hidden threats instantly with zero sampling or delays.
Cy5’s SIEM can help you to connect siloed events into attack chains—exposing advanced threats that traditional rules would overlook.
Cy5’s SIEM can auto-enrich alerts with 90+ live IOCs/TTPs—contextualize attacks using global threat actor insights.

Cy5’s SIEM transforms raw data into decisive intelligence. Our next-gen engine detects hidden threats through lightning-fast investigations, connects attack patterns across silos, and enriches findings with live global intelligence—turning complex signals into actionable defense strategies.
Cy5’s SIEM centralizes investigations: collaborate, document, and resolve incidents 90% faster in one unified SOC workspace.
Pre-built playbooks and prioritized alerts automate routine tasks, freeing analysts for critical threat hunting.
Cy5’s SIEM has 300+ native connectors for SOAR, EDR, and cloud APIs—unify tools without custom code or delays.


Stop wrestling with complex SIEMs. Cy5 delivers effortless, intelligent security operations from ingest to action. Experience zero-friction data onboarding, lightning-fast threat analysis revealing hidden risks, and unified, automated response—all proven to slash threat response by 70% and costs by 60%. Transform raw data into decisive defense with Cy5.
Cy5’s SIEM boasts tamper-proof, forensically certified logs with chain-of-custody tracking—meet legal/compliance demands effortlessly.
Cy5’s SIEM prioritizes risks by actual business impact—not generic scores—to focus resources on critical threats.
Cy5’s SIEM helps you build custom dashboards for execs, SOC, and auditors in 3 clicks—pre-loaded with PCI/GDPR templates.
Cy5’s SIEM boasts proven 70% faster threat response and 60% lower costs—with audit-proof compliance reporting built-in.

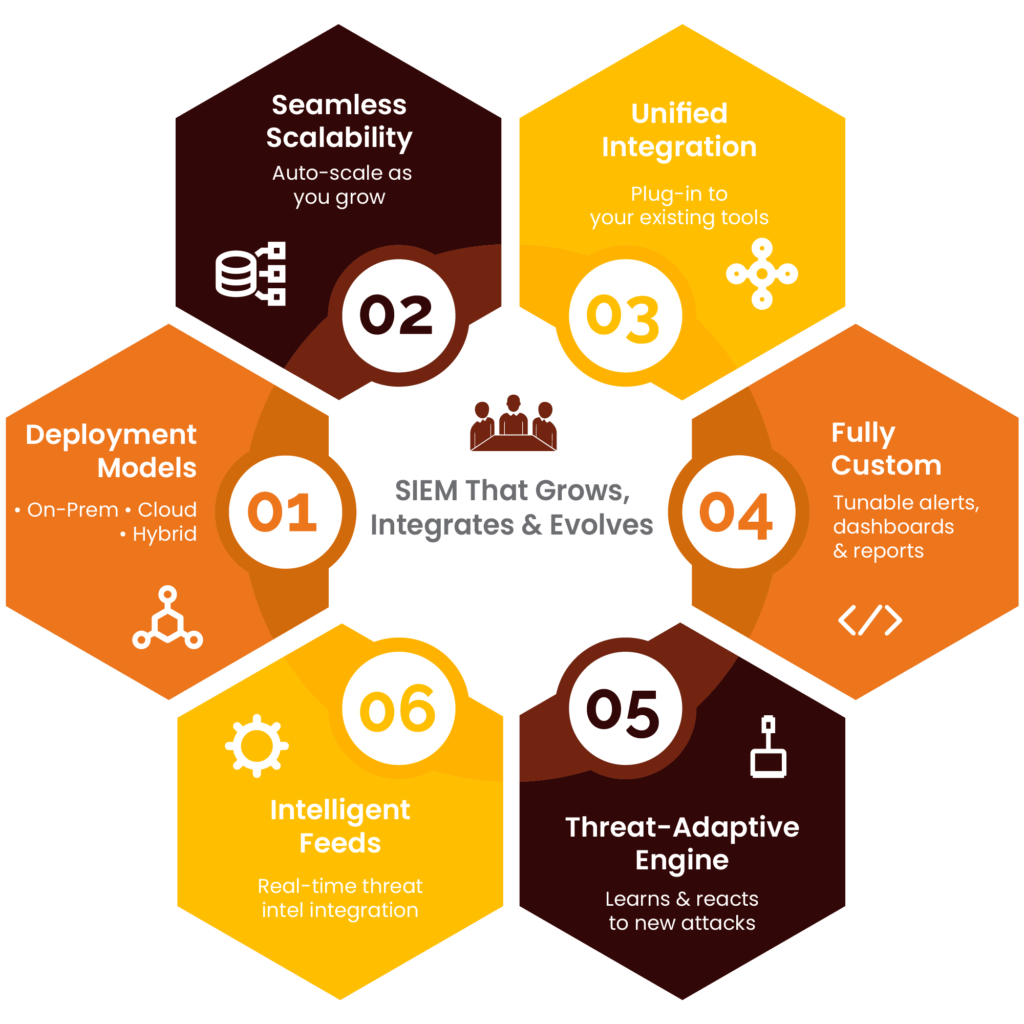
Cy5 empowers you to build a security operations foundation designed for tomorrow, not just today. Choose your path with flexible Deployment Models (On-Prem, Cloud, Hybrid) and grow effortlessly with Seamless Scalability that auto-adapts to your needs. Connect everything through Unified Integration to your existing ecosystem and make it yours with Full Customization of alerts, dashboards, and reports.
Our Threat-Adaptive Engine continuously learns to adapt instantly to emerging attacks, while Intelligent Feeds ensure you stay informed with the latest global intelligence. From the moment you start small, Cy5’s intelligent core scales big, ensuring you consistently stay secure.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Event-driven protection. Zero blind spots. Infinite scale.