The migration to the cloud has become a hallmark of modern business, offering unparalleled agility and scalability. However, this digital evolution brings with it a host of new security challenges. In 2019 alone, over 20,362 vulnerabilities were reported—an 18% increase from the previous year—highlighting a significant shift in the threat landscape. With cloud environments becoming prime targets, traditional, manual security practices simply can’t keep up with the volume and sophistication of emerging threats.
“Traditional security is like a lock on a door; AI is the smart alarm system that predicts and prevents intrusions before they happen.”
As this digital battlefield intensifies, Artificial Intelligence (AI) has stepped in as a powerful game-changer. AI-driven vulnerability management is revolutionizing cloud security, turning it from a reactive measure into a proactive, predictive, and highly automated defense. This isn’t just a technological upgrade—it’s a strategic necessity for businesses that want to safeguard their digital assets and stay ahead of increasingly complex cyber threats. In today’s rapidly evolving business world, embracing AI in security isn’t optional; it’s an essential move for future-proofing your organization.
Read More On:- Vulnerability Management in Cloud Security: A Complete Guide for 2025
Rising Stakes: Why AI is Now Essential for Cloud Security
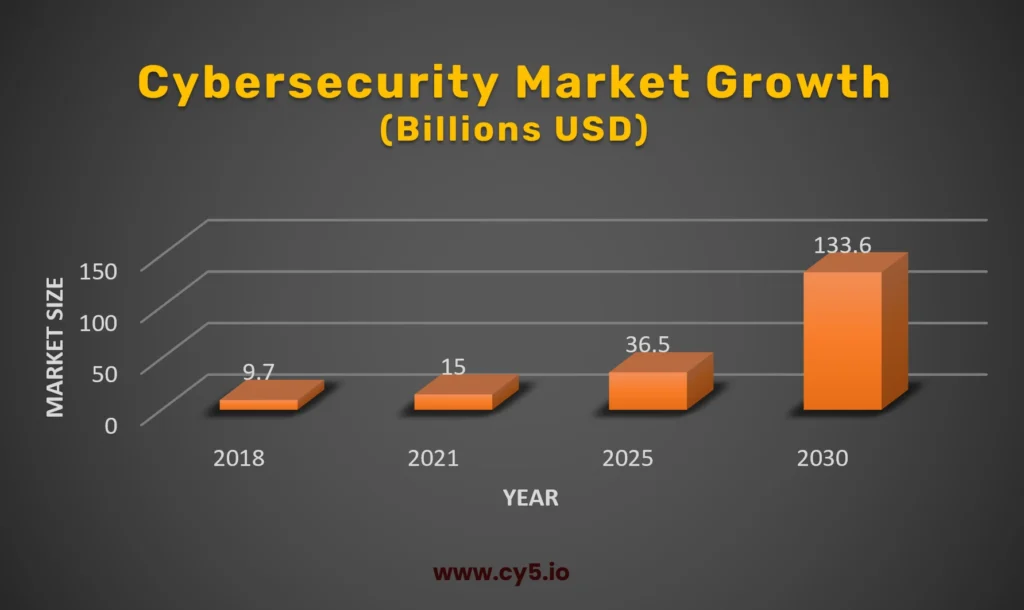
The urgency of embracing AI in cybersecurity is becoming impossible to ignore, especially in light of the rapid market growth. Research published in Decision Making: Applications in Management and Engineering highlights that the value of Artificial Intelligence in the cybersecurity sector is set to soar from USD 9.7 billion in 2018 to an eye-popping USD 133.6 billion by 2030.
This surge in investment is driven by the escalating threat landscape. Shockingly, 80% of organizations reported experiencing at least one cloud security incident in the past year, making it clear that traditional security tools are no longer up to the task. In response, AI and machine learning are proving to be the only viable solution. They offer the ability to analyze the vast amounts of data generated in cloud environments and identify threats at lightning speed—something legacy systems simply can’t keep up with. In a world where every second counts, AI isn’t just an option—it’s essential for staying ahead of cybercriminals.
How AI Revolutionizes Core Vulnerability Management Processes
AI-powered cloud security solution move beyond simple signature-based detection. They learn the unique DNA of your cloud environment to identify what’s normal and, more importantly, what’s not.
1. Proactive Threat Detection with Anomaly Detection
AI-driven threat detection excels at establishing behavioral baselines. By continuously monitoring network traffic, user logins, and application activity, AI models can identify subtle, unusual patterns that signal a zero-day attack or a novel threat vector. This capability for anomaly detection is a critical defense against attacks that bypass traditional signature-based defenses.
2. Uncovering Insider Threats with Behavioral Analytics
User and Entity Behavior Analytics (UEBA) powered by AI takes security event monitoring to a new level. By understanding typical behavior for each user and service account, AI can flag high-risk activities—like a user attempting to access sensitive data from an unauthorized location at an unusual time. This strengthens defenses against insider threats and compromised credentials.
3. Accelerating Resolution with AI-Powered Incident Response
Speed is everything in cybersecurity. AI-powered incident response automates containment and remediation workflows. Upon identifying a threat, AI systems can automatically quarantine infected containers, revoke access privileges, or even reverse unauthorized changes. This security automation dramatically shortens recovery times and minimizes the potential damage from a security breach.
4. Integrating Intelligence and Fortifying Defenses
AI doesn’t operate in a vacuum. Modern platforms integrate with global threat intelligence streams, ensuring your defenses are always updated with the latest known attack patterns and indicators of compromise. Furthermore, AI is instrumental in developing AI-based encryption strategies for complex, multi-cloud environments, ensuring data protection without sacrificing performance.
Check Out: Traditional VM vs Cloud-Native VM by Cy5
Implementing AI within Modern Cloud Security Frameworks
For maximum impact, AI should be woven into the fabric of your cloud operations. Two key frameworks facilitate this:
DevSecOps
Integrating AI into DevSecOps workflows embeds security directly into the CI/CD pipeline. AI can scan code for vulnerabilities, assess container images for risks, and validate infrastructure-as-code templates before deployment, shifting security left and reducing flaws early in the development lifecycle.
Cloud Security Posture Management (CSPM)
CSPM tools leverage AI to continuously monitor cloud configurations across accounts. They intend to automatically detect misconfigurations—a leading cause of cloud data breaches—and recommend fixes, ensuring compliance with security policies and frameworks.
Are You Looking for Most Efficient CSPM Solution?
Check out Cy5’s CSPM
Navigating the Challenges: The Road to AI Implementation
While the benefits are clear, implementing AI is not without its hurdles. Research highlights several critical barriers to implementing AI against cyber threats:
- Lack of Quality Data (47%): AI models are only as good as the data they train on. Incomplete or noisy data can lead to inaccurate predictions.
- Integration Challenges (36%): Embedding new AI tools into existing cloud security frameworks and SIEM systems can be complex.
- Skills Gap in AI Cybersecurity (31%): There is a significant shortage of professionals who understand both cybersecurity and data science.
Ethical and Privacy Considerations
Using AI for monitoring raises important questions about user privacy and the ethical use of data, which must be governed by clear policies.
Acknowledging and planning for these challenges is essential for a successful AI transformation.
Future-Proofing: AI’s Role in Mitigating Emerging Cloud Threats
As threats evolve, so do AI’s applications. The research identifies emerging threats where AI is critical for defense:
- Cloud Hacks via On-Premises Compromises: AI can correlate events across hybrid environments, detecting if an on-premises breach is being used to pivot into the cloud.
- Container Vulnerabilities: AI tools scan container registries to identify images with known vulnerabilities or malicious code before they are deployed.
- API Risks: AI monitors API traffic to detect and block abnormal calls that indicate abuse or exploitation.
- DDoS Attacks: AI algorithms can analyze traffic patterns in real-time to identify and mitigate large-scale DDoS attacks before they cause downtime.
Must Read: Cloud Security Best Practices for 2025
Conclusion: AI as a Strategic Imperative
The integration of Artificial Intelligence in cybersecurity is no longer a futuristic concept—it is a present-day necessity for robust vulnerability management. By enabling proactive threat detection, automating incident response, and enhancing cloud-native security tools, AI empowers organizations to build a resilient and adaptive security posture.
The journey requires navigating data quality, integration, and talent challenges. However, the result—a cloud environment that can learn, adapt, and defend itself at scale—is the ultimate competitive advantage in the digital age. Embracing AI is the key to turning the tide against cyber adversaries and securing the future of the cloud.
Source: Insights and data referenced in this article are based on the study “AI-Driven Vulnerability Management: Strengthening Cloud Security Posture” by Abhilash Reddy and Pabbath Reddy, published in Decision Making: Applications in Management and Engineering, Volume 7, Issue 2 (2023). Retrieved from Academia.edu
FAQs: AI-Powered Vulnerability Management & Cloud Security
Modern cloud vulnerability management is a continuous, proactive process that identifies, assesses, prioritizes, and remediates security weaknesses in dynamic cloud environments. Unlike traditional methods, it leverages artificial intelligence and automation to keep pace with the scale and speed of the cloud, shifting from a reactive cost center to a strategic, integrated business function.
AI revolutionizes threat detection by moving beyond static signatures. It uses machine learning to establish a behavioral baseline of your unique cloud environment, enabling it to identify subtle, anomalous activities that indicate novel threats, zero-day attacks, or advanced persistent threats (APTs) that traditional tools would miss.
Behavioral analytics, specifically User and Entity Behavior Analytics (UEBA) powered by AI, enhances security event monitoring by learning the normal patterns for every user and service account. It can then flag high-risk anomalies, such as a user accessing sensitive data from an unusual location, effectively uncovering insider threats and compromised credentials.
AI-powered incident response automates containment and remediation workflows. Upon detecting a threat, the system can instantly execute actions like quarantining infected containers, revoking access privileges, or rolling back unauthorized changes. This security automation dramatically shortens mean time to resolution (MTTR) and minimizes breach impact.
Absolutely. AI excels at security event correlation across hybrid environments. It can analyze data from both on-premises systems and cloud platforms to detect when a breach in a traditional network is being used as a pivot point to launch an attack on cloud assets, providing a unified defense posture.
AI integrates directly into DevSecOps workflows by automatically scanning container registries and images for known vulnerabilities, misconfigurations, or malicious code before they are deployed into production. This “shifts security left,” ensuring risks are identified and remediated early in the development lifecycle.
The three primary challenges are:
1) Lack of Quality Data (47%), as AI models require clean, comprehensive data to be effective;
2) Integration Challenges (36%) with existing tools; and
3) a significant Skills Gap in AI Cybersecurity (31%), where professionals proficient in both data science and security are scarce.
By understanding the nuanced context of normal network and user behavior, AI can more accurately distinguish between legitimate activity and genuine threats. This contextual intelligence significantly reduces false positives (alert fatigue) and false negatives (missed threats) compared to rule-based systems.
Using AI for monitoring raises important questions about user privacy and data governance. Organizations must implement clear policies on data usage, retention, and transparency to ensure ethical AI deployment that protects against threats without infringing on individual privacy rights.
With 80% of organizations reporting a cloud security incident last year, legacy tools are insufficient. AI provides the only viable solution to analyze vast cloud data at speed, automate responses, and predict novel attacks. It transforms security into a competitive advantage, enabling a resilient, self-defending cloud environment.