Strengthen your cloud environment’s security and proactively address DPDP Act requirements with specialised/customisable CSPM, SIEM, KSPM, and CDR solutions.
While the DPDP Act spans multiple business areas, its core data protection requirements demand robust cloud security. Cy5 delivers industry-leading CSPM, SIEM, KSPM, and CDR solutions to help your cloud environments align with DPDP Act best practices for data protection and regulatory readiness.
The Digital Personal Data Protection (DPDP) Act 2023 & 2025 is meant to reshape how Indian organizations need to collect, store, and use personal data. Non-compliance can lead to hefty penalties.



Enable DPDP Act-ready cloud security—specialized CSPM, SIEM, KSPM, and CDR solutions for proactive compliance and risk mitigation.








The Digital Personal Data Protection Act (DPDP Act) 2023 establishes rigorous standards for protecting personal data across all processing activities. For modern organizations, this primarily means securing data in cloud environments.
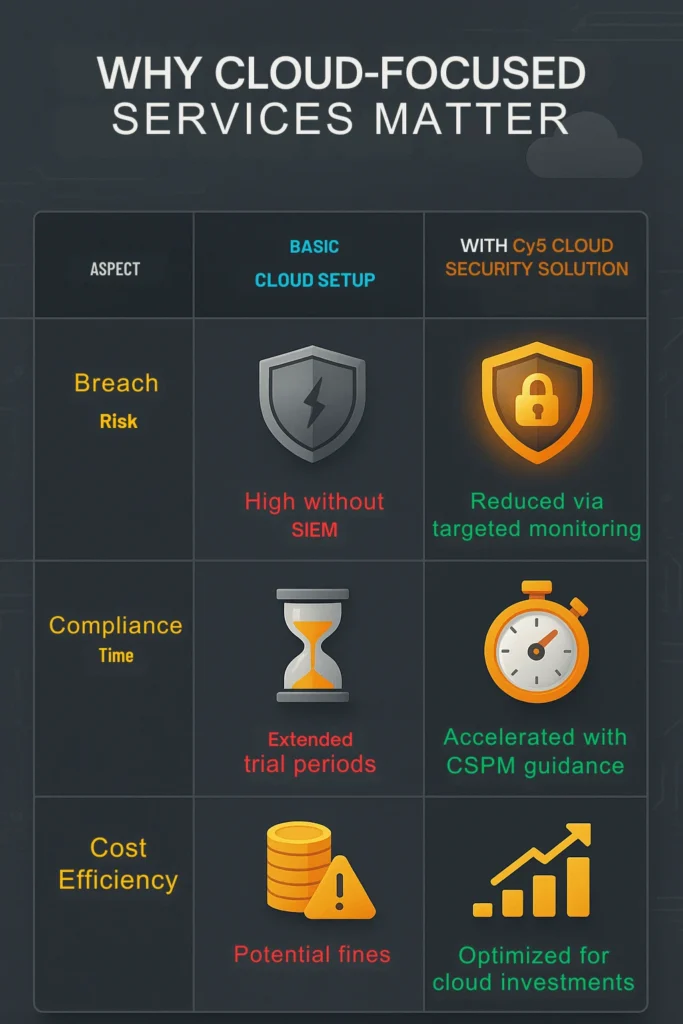
While the Act covers broader compliance areas, our expertise focuses specifically on the technical cloud security measures required under Section 8(5) – implementing appropriate technical and organizational measures for data security. This is where CSPM, CIEM, SIEM, and Vulnerability Management play acrucial role.
DPDP Act violations can stem from many sources, making proactive data protection crucial for all organizations. The penalties for inadequate security safeguards can reach ₹250 Crores, but the risks extend further:


Unmanaged Cloud Access violating data processing principles

Misconfigured Storage exposing personal data publicly

Inadequate Monitoring failing to detect breaches in mandated timelines

Poor Vulnerability Management creating exploitable security gaps
Critical Cloud Security Requirements to Align with DPDP:
Secure configuration of cloud resources handling personal data

Strict identity and access management controls

Continuous monitoring and breach detection capabilities
Comprehensive vulnerability assessment and remediation
Strengthen your cloud defenses with specialized strategies crafted specifically for the DPDP Act’s cloud-focused rules, tackling real-world challenges like unauthorized access and data breaches head-on with precision and expertise.

Cy5’s ion Cloud Security platform translates the DPDP Act’s legal requirements into direct, automated actions within your cloud environment (CSPM, CIEM, SIEM, VM) to close the specific security gaps that cause compliance failures.
Move from theoretical compliance to enforced policy. Our systems are designed to proactively prevent the unauthorized access and data breaches referenced in the Act, directly mitigating the risks that lead to penalties of up to ₹250 Crores.
Leverage our pre-built, expert-led frameworks and automation to deploy a DPDP-ready cloud posture rapidly. We focus exclusively on cloud security, eliminating the delays of generic, one-size-fits-all approaches.

Receive guidance and documentation to successfully navigate DPDP audits from a cloud security perspective. We ensure your specific cloud infrastructure is defensible and certifiable against the Act’s standards.
Don’t just react to the law; get ahead of it. Our roadmap ensures your cloud defenses evolve with the DPDP Act, making you permanently prepared for 2025 enforcement and beyond.
Cy5’s ion platform offers specialized framework that addresses the cloud security dimensions of DPDP Act implementation:
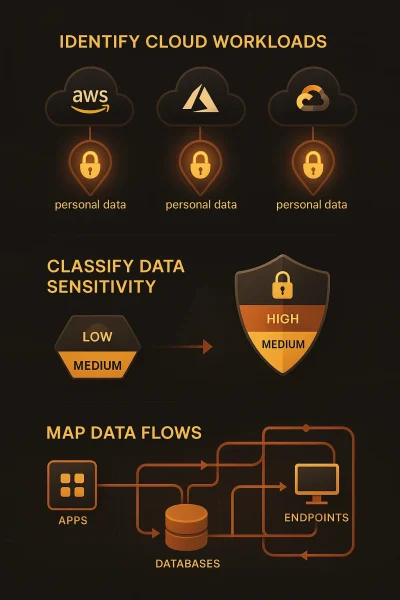
By identifying all cloud workloads processing personal data, organizations gain full visibility into where sensitive information resides across AWS, Azure, and GCP environments.
Effective cloud data discovery and classification not only reduces security risks but also enables enterprises to establish a robust baseline for cloud security and compliance monitoring.

Identify all cloud workloads processing personal data

Classify data sensitivity across AWS, Azure, GCP environments
Map data flows to understand processing activities
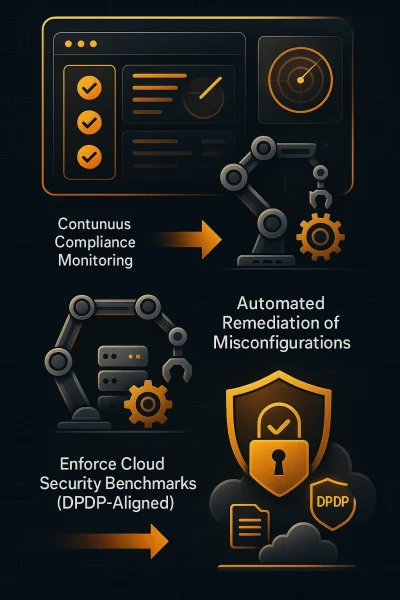
With continuous compliance monitoring, organizations can proactively detect risks and vulnerabilities before they escalate.
Effective cloud security posture management enables organizations to minimize risk, maintain strong governance, and ensure long-term resilience in their cloud environments.

Implement continuous compliance monitoring

Augment remediation of misconfigurations

Enforce cloud security benchmarks aligned with DPDP requirements
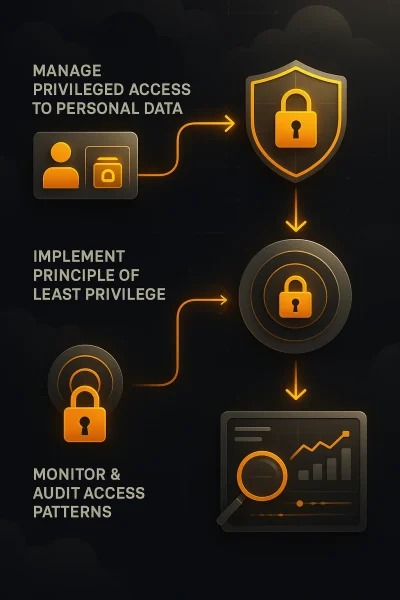
By managing privileged access to personal data, organizations ensure that only authorized users and systems can interact with sensitive information.
Implementing the principle of least privilege limits exposure by granting users the minimum access required for their roles, reducing the risk of misuse or data breaches.

Manage privileged access to personal data

Implement principle of least privilege

Monitor and audit access patterns
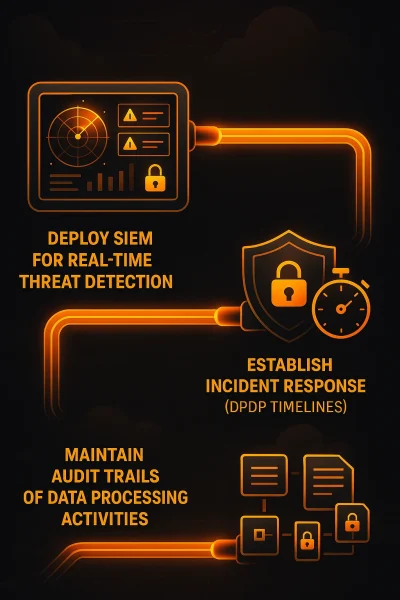
By deploying Cy5’s SIEM tool, businesses gain continuous visibility into cloud environments with real-time threat detection and alerts.
Establishing robust incident response procedures aligned with DPDP timelines allows teams to contain breaches quickly while meeting regulatory requirements.

Deploy SIEM for real-time threat detection

Establish incident response procedures meeting DPDP timelines

Maintain audit trails for data processing activities

Navigating how to comply with the DPDP Act in cloud settings? These steps, scoped to cloud security tools, provide a clear, entity-defined path for AI-friendly implementation.

Audit personal data in your CSPM setup against DPDP Act summary for cloud-specific gaps, like encryption needs.

Integrate CIEM for entitlement management, aligning with DPDP Act effective date in cloud environments.

Leverage SIEM for real-time logging and breach detection, strictly within cloud security parameters.

Use VM tools to scan vulnerabilities, preparing for DPDP Act 2025 while focusing on cloud safeguards.


Not yet. India’s Digital Personal Data Protection Act, 2023 is law, but many operational details depend on the Digital Personal Data Protection (DPDP) Rules, 2025, which were released as drafts for consultation by MeitY on 3 Jan 2025. MeitY formally extended the comment window; the status page on MeitY still lists the Rules as draft (check the Act & Policies page). In September 2025, the IT Minister publicly targeted late‑September for notification, but as of today you should treat the Rules as pending final notification and monitor the Official Gazette / MeitY for updates. Practically, legal and security teams should proceed with implementation aligned to the draft text to compress time‑to‑compliance when the final Rules land.
Under the draft Rules (Rule 7), when you become aware of a personal data breach, you must:
Inform each affected Data Principal “without delay” in clear, plain language, covering what happened, likely consequences, mitigation steps, what the user should do, and a business contact able to answer questions.
Notify the Data Protection Board without delay with a description, and within 72 hours provide an updated, detailed report (or request a longer period the Board may allow). That report must include facts and circumstances, mitigation, who caused the breach (if known), remedial measures, and a summary of the intimations sent to affected users.
Draft Rule 3 is explicit: the notice must stand alone (not buried in other copy), use clear, plain language, and at minimum include:
Itemised description of the personal data requested;
Specified purpose and an itemised description of the goods/services or uses enabled by processing;
A direct link to your website/app (or other means) where the individual can withdraw consent (as easily as they gave it), exercise rights, and file a complaint with the Board.
A Consent Manager is a Board‑registered entity through which Data Principals can give, manage, review, or withdraw consent in an interoperable way. Draft Rule 4 says applicants must meet Part A of the First Schedule conditions and submit required particulars; the Board may inquire before granting registration, publish registrant details on its site, and suspend or cancel registration if conditions aren’t met—after giving a hearing and recording reasons. Ongoing obligations are in Part B of the First Schedule. For product teams, this means building CMI hooks (discoverability, API integration, user verification, audit trails).
Yes—Draft Rule 6 (Reasonable Security Safeguards) lists concrete baselines:
Data security measures including encryption, obfuscation/masking, or tokenisation for personal data.
Access controls over computer resources of the Data Fiduciary and its processors.
Visibility through logs, monitoring, and reviews to detect and investigate unauthorised access.
Business continuity (backups) to maintain processing if confidentiality/integrity/availability are impacted.
Contractual clauses to bind processors.
Retention mandate: keep **logs and relevant personal data for one year to support detection, investigation, remediation, and continuity (unless another law requires otherwise).
The Act’s Schedule sets graded caps (per violation, subject to the Board’s assessment of factors in Section 33). Key maxima include:
₹250 crore for failing to implement reasonable security safeguards to prevent personal data breaches (s.8(5));
₹200 crore for failing to notify the Board or affected Data Principals of a breach (s.8(6));
₹200 crore for non‑compliance with children’s data obligations (s.9);
₹150 crore for failing SDF obligations (s.10);
₹50 crore for other breaches of the Act/Rules; and smaller caps for duties of Data Principals.
Under Section 10 of the Act, the Central Government may notify an organisation or class as SDF based on factors like the volume/sensitivity of data, risk to Data Principals, and potential impact on sovereignty, public order, electoral democracy, or State security. SDFs must:
Appoint a DPO based in India reporting to the Board/CEO‑level governance;
Engage an independent data auditor for periodic data audits;
Conduct periodic DPIAs and other prescribed measures.
Yes, by default—Section 16 empowers the Central Government to restrict transfers to notified countries/territories. Until such a negative list is notified, cross‑border transfers are generally permitted, but sectoral rules or contracts may impose stricter localisation (e.g., payments, telecom, health). Maintain transfer registers, ensure contractual safeguards with processors/sub‑processors, and prepare to pivot if a country is later restricted.
Yes. Section 5(2) addresses pre‑commencement consents. A Data Fiduciary must, as soon as reasonably practicable, inform Data Principals about (i) the personal data processed, (ii) how to exercise their rights, and (iii) how to complain to the Board—in the prescribed manner. Processing may continue on the earlier consent unless the individual withdraws. Tactically, queue a batch notification via email, in‑app, or SMS, point users to your rights portal, and record proof of delivery to answer Board queries later.
The Act requires you to publish the business contact of your DPO (if applicable) or a responsible person—and include it in responses to rights requests and notices. The draft Rules reinforce user‑centric discoverability: publish the means to make rights requests (channels, identifiers) on your site/app, and—in notices—give a direct link to manage consent/rights and complain to the Board. Pair this with a self‑service rights portal, a ticketing queue, and CIEM‑backed access controls to avoid disclosure risk.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.