Cloud transformation has revolutionized how enterprises innovate, scale, and deliver value. Yet, behind the promise of agility and cost efficiency lies a stark reality — the cloud is now one of the most targeted frontiers of cyber warfare. As more critical systems move to multi-cloud and hybrid architectures, the challenge for business leaders isn’t just managing data, but defending it.
In today’s volatile cyber landscape, cloud vulnerabilities can translate into boardroom crises overnight. Defending cloud platforms against cyberattacks isn’t a one-time initiative — it’s a continuous, intelligence-driven discipline that merges technology, governance, and human readiness.
This article explores the evolving cybersecurity challenges in cloud computing, major threat vectors shaping enterprise exposure, and actionable strategies to help organizations build a multi-layered, future-ready cloud defense.
The Expanding Cloud Landscape — Why Security Has Become a Boardroom Priority
Imagine a C-suite executive in 2025, poring over dashboards showing petabytes of data flowing seamlessly across AWS, Azure, and Google Cloud. This agility fuels growth, slashing costs by up to 30% and accelerating time-to-market. Yet, beneath this efficiency lies a shadow: the cloud’s vast, interconnected nature amplifies risks, turning minor oversights into multimillion-dollar catastrophes.
Cloud computing has redefined modern enterprise infrastructure. From software delivery to data analytics, the cloud enables businesses to move faster and smarter. But this convenience comes at a price: a broader attack surface. Consider the economic ripple: global cloud spending is projected to hit $1 trillion by 2030, but so too are cyber losses, estimated at $10.5 trillion annually.
Enterprises now operate in a dynamic ecosystem of IaaS, PaaS, and SaaS environments, each with its own security dependencies and shared responsibility models. Misconfigured storage buckets, unsecured APIs, and weak access controls can expose sensitive data — often without a single system being “hacked” in the traditional sense.
The shift toward remote work, third-party integrations, and automation has further blurred the perimeter. For executive teams, cloud security has become more than an IT issue — it’s a strategic business imperative tied directly to brand trust, compliance, and operational continuity.
Unmasking the Hidden Vulnerabilities of Modern Cloud Infrastructure
1. Multi-Tenancy and Shared Responsibility Gaps
Multi-tenant cloud environments allow multiple customers to share computing resources. While cost-effective, this setup creates interdependency risks — where a single misconfiguration or vulnerability in one tenant can expose others.
Many enterprises still misunderstand the shared responsibility model. Cloud providers secure the infrastructure, but clients remain accountable for data protection, identity management, and configuration hygiene. That blurred line is often where breaches begin.
2. Misconfigurations, Access Control Failures, and Patching Pitfalls
According to leading security assessments, misconfigurations account for over 30% of cloud data breaches. These often stem from rushed deployments or overlooked permissions.
Unpatched virtual machines, orphaned storage, and exposed APIs can create invisible entry points for attackers. In complex multi-cloud setups, even minor missteps can cascade into widespread exposure.
A disciplined approach to configuration management, continuous patching, and access governance is non-negotiable for resilient cloud defense.

Major Cloud Security Incidents: Lessons from Global Breaches
The last decade has seen a wave of high-profile cloud cyberattacks — each one underscoring how human error, misconfigurations, or delayed response can cripple even the most advanced organizations.
- Capital One Breach (2019): A simple misconfiguration in a web application firewall exposed over 100 million customer records, proving that automation without governance invites disaster.
- AWS S3 Bucket Leaks: Numerous global enterprises have unintentionally exposed databases due to public S3 settings, illustrating how minor oversights in configuration can undermine billion-dollar infrastructures.
- Code Spaces Attack (2014): A DDoS and extortion attack forced the shutdown of an entire company within days, highlighting the need for robust backup and disaster recovery strategies.
Each of these events shares a common thread — the gap between cloud adoption speed and security readiness. The takeaway? Enterprises must treat defending cloud platforms as an integrated, continuous process — not an afterthought.
| Incident Type | Percentage of Cloud Breaches | Key Lesson |
|---|---|---|
| Data Breaches | 33% | Prioritize encryption and access audits to prevent exfiltration. |
| Environment Intrusions | 27% | Implement zero trust to block lateral movement. |
| Data Leaks | 28% | Automate configuration checks to catch public exposures early. |
| Cryptomining | 23% | Monitor for anomalous compute usage to detect stealthy resource hijacks. |
| Compliance Violations | 25% | Align with standards like NIST to avoid regulatory pitfalls. |
| Failed Audits | 15% | Schedule quarterly penetration tests for proactive gap-closing. |
| Downtime from Misconfigs | 34% | Use infrastructure-as-code for version-controlled, auditable setups. |
Building a Multi-Layered Defense Strategy for Cloud Environments
Proactive Monitoring and Threat Intelligence
\Reactive defense is no longer sufficient. Enterprises must deploy real-time monitoring, SIEM integration, and behavioral analytics to detect anomalies before they escalate.
Leveraging threat intelligence feeds allows organizations to anticipate attacks rather than merely respond to them. Cy5.io’s adaptive intelligence framework, for example, enables clients to correlate global threat data with their specific cloud footprint — transforming visibility into predictive defense.
Zero Trust and Access Governance
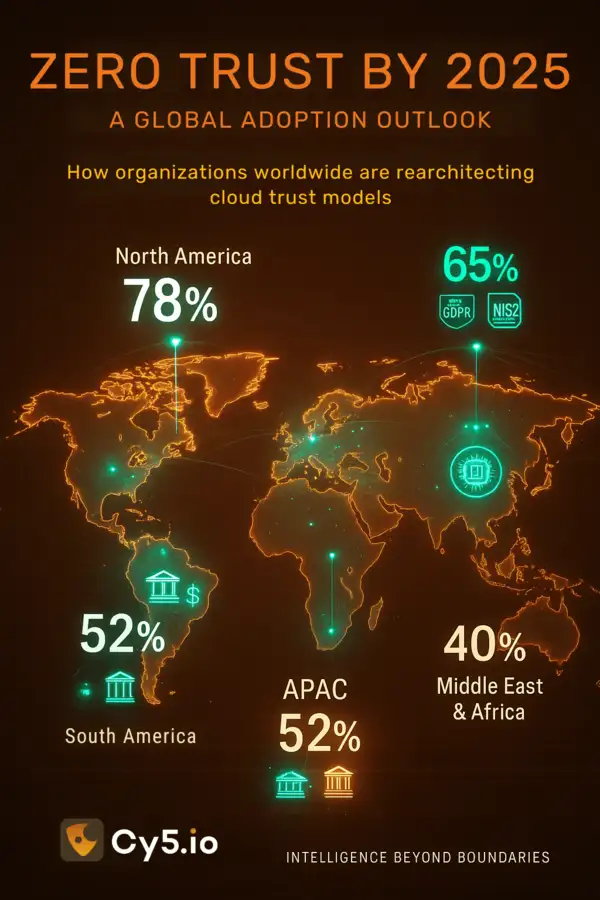
Modern security leaders are embracing Zero Trust architecture — assuming breach rather than assuming trust.
This means enforcing least privilege access, continuous verification, and segmentation across all layers of the cloud.
Multi-factor authentication (MFA), role-based access control (RBAC), and centralized identity and access management (IAM) reduce the blast radius of compromised credentials.
Encryption, MFA, and Incident Response Readiness
Data should be encrypted both in transit and at rest. Native encryption offered by cloud providers is a baseline — but enterprises should also integrate end-to-end encryption and key management solutions for high-value assets.
A tested incident response plan ensures rapid containment and recovery when breaches occur. Regular simulations and tabletop exercises prepare teams to act decisively under pressure.
Network Segmentation and Continuous Patching
Segmenting networks prevents attackers from moving laterally once they breach a single node. Complementing this with automated patch management closes exploitable gaps quickly.
As vulnerabilities emerge faster than ever, agility in patching has become a core metric of cyber resilience.
Case Study: Singapore’s Model for National Cloud Security Governance
Singapore has emerged as a global benchmark for cloud cybersecurity governance. Through the Cyber Security Agency (CSA) and the Personal Data Protection Act (PDPA), it enforces a culture of accountability and compliance across both public and private sectors.
The Multi-Tier Cloud Security (MTCS) framework, built on ISO/IEC 27001 standards, certifies providers based on their security maturity — offering organizations confidence in vendor integrity.
Singapore’s collaborative model — connecting government agencies, academia, and enterprises — demonstrates how collective intelligence and policy integration can elevate national cloud defense.
The lesson for enterprises worldwide: cybersecurity is not a siloed function. Effective protection arises from shared intelligence, aligned governance, and a commitment to continuous learning.

The Future of Cloud Defense — AI, Automation, and Global Collaboration
The next phase of cloud defense will be defined by autonomous detection, AI-driven analysis, and global data collaboration.
AI and machine learning are already transforming threat hunting and anomaly detection, identifying suspicious behaviors invisible to human analysts. Combined with automation, they enable organizations to contain incidents in seconds rather than hours.
Meanwhile, international coalitions like the Cloud Security Alliance (CSA) and NIST’s cloud security frameworks are shaping best practices for cross-border data protection and cyber resilience.
As emerging threats grow in sophistication — from supply-chain attacks to AI-powered phishing — enterprises that embrace automation and shared intelligence will lead the next era of defensible innovation.
Key Takeaways for Cyber Leaders
To remain resilient in an increasingly hostile cloud environment, cyber leaders should:
- Reinforce the shared responsibility model — ensure teams understand where provider accountability ends and client security begins.
- Adopt Zero Trust principles — assume every connection and device must be verified.
- Implement continuous monitoring and threat intelligence — visibility is defense.
- Encrypt everything, everywhere — treat encryption as a standard, not an option.
- Test incident response plans regularly — practice is the difference between chaos and control.
- Invest in employee awareness — technology fails when people aren’t trained to recognize risk.
Enterprises that follow these principles position themselves not only to survive attacks but to thrive through resilience — maintaining trust, compliance, and operational strength even amid disruption.
Final Thoughts — Building Resilient Cloud Security with Cy5.io
Defending the cloud isn’t just about technology — it’s about foresight. The cloud will continue to power digital transformation, but without a parallel investment in security intelligence, adaptive defense, and human expertise, innovation becomes exposure.
At Cy5.io, we empower organizations to see beyond the perimeter, integrating real-time intelligence, automation, and cloud-native defense strategies that turn insight into protection.
In an age where cyber threats evolve by the hour, visibility, collaboration, and proactive defense are the ultimate competitive advantages.
Inspiration Resource: Krishnamurthy, N., & Parvatham, S. (2023). Exploring the Cloud: Vulnerabilities and Cybersecurity Challenges. International Journal on Recent and Innovation Trends in Computing and Communication. Retrieved from Google Scholar
FAQs: Defend the Cloud
The biggest culprits are publicly exposed storage, over-permissive IAM, unencrypted data, weak keys/secrets handling, and disabled logging. Root cause is usually human error and fragmented ownership across multi-cloud. CSA notes misconfig and human error remain leading breach factors—continuous monitoring and centralized logging materially reduce risk.
\Standardize secure baselines, enforce least-privilege IAM, turn on encryption by default, and enable centralized logs + anomaly detection. Add automated checks (CSPM/CNAPP) and periodic human review.
CNAPP is an integrated platform that unifies CSPM (posture), CWPP (workload protection), and CIEM (identity/entitlement) so teams can prioritize risk across apps, identities, and data in one place. It’s designed for cloud-native environments where siloed tools miss cross-domain risk.
Multi-cloud sprawl, identity explosion, misconfigurations, neglected assets, and data exposure—plus new AI/agentic risks. Industry reports highlight widespread plaintext data and governance gaps across enterprises.
Cloud adoption is near-universal, with a majority of workloads already in cloud and rising. That scale pushes identity, posture, and data controls to the top of the security roadmap.
Deploy a CSPM or CNAPP to continuously scan configs against best practices and compliance baselines; feed findings to SIEM for alerting and investigation. Keep humans in the loop—automation + analyst review performs best
Treat every identity, device, and workload as untrusted; verify continuously with strong IAM, policy-based access, micro-segmentation, and runtime monitoring. Adoption is accelerating as boards push for modernization and SASE/SSE roadmaps.
Enable centralized logging, API audit trails, and anomaly detection across clouds; route to SIEM with retention that supports forensics and regulatory requirements. These controls are explicitly recommended by cloud security alliances and NIS2 guidance.
NIS2 mandates risk management measures (access control, patching, incident reporting, supply-chain oversight). ENISA provides technical implementation guidance organizations can align to today.
MAS-TRM (2021) guides governance, IAM, patching, incident response, and third-party risk; cloud providers map controls to help implementation. While some parts are guidance, specific Notices can be binding—check your regulator’s scope.
Least-privilege IAM + JIT access, prevent public exposure by default, encrypt at rest/in transit, and continuous posture scanning. Pair with playbooks for rapid remediation.
Yes—SSE helps enforce Zero Trust access for users/apps from the edge, and adoption is now a formal corporate initiative for most organizations. Integrate identity, data, and threat controls via SSE to reduce attack surface.
Map CNAPP/CSPM checks to NIS2 risk-management measures (access control, vulnerability management, logging, incident reporting). Use SIEM for evidence and audit trails.
Pre-stage IR runbooks per cloud provider, enable forensic logging, rehearse isolation/rollback, and coordinate with your CSPM/CNAPP + SIEM for enrichment. IR speed is a known weakness in cloud without this prep.
Treat AI agents like interns with restricted privileges; enforce runtime policy, tool sandboxing, and secrets isolation. Identity governance must scale as machine identities outnumber humans.
% critical misconfigs open >30 days, mean time to remediate (MTTR), % identities with admin rights, % assets with encryption/logging enabled, drift from baseline by business unit, and compliance coverage. (Backed by CSA guidance on centralized logging and posture baselines.)