TL;DR
CDR focuses on detecting and responding to threats inside cloud environments (IaaS/PaaS/SaaS, containers, serverless) using cloud‑native telemetry. XDR unifies detections and response across domains (endpoints, network, identity, email and cloud). Use CDR for deep cloud visibility; use XDR to correlate signals enterprise‑wide.
As organizations rapidly migrate to cloud infrastructures, the security landscape has become increasingly complex. With 99% of cloud security failures attributed to customer misconfigurations and a projected 300% increase in cloud-targeted cyber threats by 2025, choosing the right detection and response solution has never been more critical. Security teams face a pivotal decision: should they invest in Cloud Detection and Response (CDR) or Extended Detection and Response (XDR)?
Both technologies promise unified threat visibility and faster response times, but they approach the problem from fundamentally different angles. While XDR casts a wide net across your entire digital infrastructure, CDR dives deep into the unique complexities of cloud-native environments. The question isn’t which one is better—it’s which one (or both) fits your organization’s cloud security architecture.
What Is Cloud Detection and Response (CDR)?
Cloud Detection and Response (CDR) is a cloud-native security solution specifically designed to identify, analyze, and respond to security threats within cloud environments. Unlike traditional security tools built for static on-premises infrastructures, CDR addresses the unique challenges of dynamic, distributed cloud architectures including ephemeral workloads, containerized applications, and serverless functions.
Picture this: Your organization has fully embraced AWS, Azure, and GCP, spinning up ephemeral containers and serverless functions like clockwork. But amid the innovation, visibility evaporates. CDR is like a vigilant air traffic controller for your cloud airspace. It ingests telemetry from cloud-specific sources—think API calls, control plane logs, workload metadata, and identity activities—to spot anomalies in real time.
Core Capabilities of CDR
Real-Time Threat Detection
- CDR watches cloud setups non-stop with smart algorithms spotting bad behaviors or setups in real time.
- It pulls in data from spots like AWS CloudTrail, Kubernetes logs, Azure Monitor, and VM happenings.
- Key alerts catch things like rising privileges, odd network flows, or sneaky side moves.
Automated Response Mechanisms
- CDR auto-handles threats by isolating hit systems or locking down workloads right away.
- It tweaks network rules or rebuilds setups from safe backups without human help.
- All via cloud APIs for quick, hands-off fixes to contain dangers fast.
Comprehensive Cloud Visibility
- CDR offers complete oversight of cloud setups, covering VMs, containers, serverless, networks, storage, and service tweaks.
- It lets teams connect identity moves, runtime happenings, and provider logs for deeper checks.
- Spotting linked threats becomes easier, revealing sneaky attack flows.
Cloud-Centric Risk Monitoring
- CDR stays on top of cloud setups, spotting setup errors, compliance slips, and exploitable gaps.
- It flags these risks upfront, nipping threats in the bud before hackers pounce.
- Overall, this builds a tougher cloud shield, keeping dangers at bay.
Also Read: What Is Cloud Detection and Response (CDR)? The Complete 2025 Guide
Key Benefits of Implementing CDR
Organizations implementing CDR solutions experience transformative improvements in their cloud security capabilities:
- Reduced Cloud Breach Risk: Proactively identifying and mitigating vulnerabilities before unauthorized access occurs
- Faster Threat Detection: Mean time to detect (MTTD) drops significantly with real-time monitoring and AI-powered analysis
- Minimized Blast Radius: Swift detection and automated response contain incidents before they spread across cloud resources
- Enhanced Compliance: Continuous monitoring helps maintain compliance with regulations like PCI DSS, HIPAA, and GDPR
- Scalable Security: CDR adapts seamlessly as cloud resources scale up or down, ensuring consistent protection
CDR Use Cases
CDR excels in scenarios specific to cloud environments:
- Cloud Security Monitoring: Continuously tracking user and service activity across hybrid and multi-cloud deployments
- Threat Hunting in the Cloud: Searching historical data for indicators of advanced persistent threats (APTs)
- Third-Party Cloud Activity Monitoring: Detecting unauthorized access from known malicious sources or monitoring heightened activity from business partners
- Detection of Unauthorized Changes: Identifying unauthorized modifications to cloud configurations that could lead to exposure
- Multi-Cloud Security: Providing unified visibility and response across AWS, Azure, and Google Cloud Platform
Actionable Item: Do-It-Yourself (DIY): 15-Min CLI AWS/GCP/Azure Cloud Posture Checklist
What Is Extended Detection and Response (XDR)?
Extended Detection and Response (XDR) is a unified security solution that provides comprehensive threat detection and response capabilities across multiple security layers. As Gartner defines it, XDR is “a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components”.
Unlike traditional point solutions that operate in silos, XDR integrates security data from endpoints, networks, cloud workloads, email, identity systems, and applications to deliver a holistic view of an organization’s threat landscape.
Core Capabilities of XDR
Unified Data Collection and Correlation
- XDR pulls in and standardizes tons of data from all sorts of security gear across your tech setup.
- It links up events from those old isolated spots to spot tricky threats.
- This way, it catches fancy, multi-angle attacks that lone tools skip.
Advanced Threat Detection
- XDR leans on AI and ML to sift data and link events, nabbing known threats plus sneaky unknowns.
- Behavioral checks flag weird patterns hinting at bad actors.
- Sharpens threat spotting while ditching false alarms.
Automated Investigation and Response
- XDR sorts threats by risk level, helping analysts tackle the worst ones first.
- Auto-moves include cutting off bad endpoints, freezing accounts, or halting shady traffic.
- This setup speeds triage, keeping responses quick and on point.
Cross-Domain Visibility
- XDR blends info from endpoints, networks, clouds, emails, and ID systems for sharp attack surface views.
- Teams get a full picture to track side-to-side moves and login hacks.
- This catches sneaky threats that single tools miss.
Key Benefits of Implementing XDR
Organizations deploying XDR solutions realize significant operational and security improvements:
- Enhanced Threat Detection: XDR’s cross-platform visibility and correlation capabilities identify 81% of threats faster than traditional approaches
- Reduced Alert Fatigue: By consolidating multiple security alerts into a unified view and filtering false positives, XDR enables analysts to focus on genuine threats
- Improved Incident Response: Detailed cross-domain threat context and automated workflows accelerate investigation and remediation processes
- Operational Efficiency: Automation of repetitive security tasks frees security teams to focus on higher-value initiatives
- Simplified Security Management: A single platform for managing security operations across different environments reduces complexity
XDR Use Cases
XDR proves particularly valuable in these scenarios:
- Multi-Stage Attack Detection: Identifying coordinated attacks that span multiple attack vectors (phishing email → compromised endpoint → lateral movement → data exfiltration)
- Insider Threat Detection: Leveraging User and Entity Behavior Analytics (UEBA) to identify anomalous insider behaviors
- Ransomware Response: Detecting pre-ransomware activities and disrupting kill chains before encryption occurs
- Compliance Reporting: Generating comprehensive audit trails and compliance reports across the entire security infrastructure
- Hybrid Infrastructure Security: Bridging detection gaps between on-premises IT and cloud services
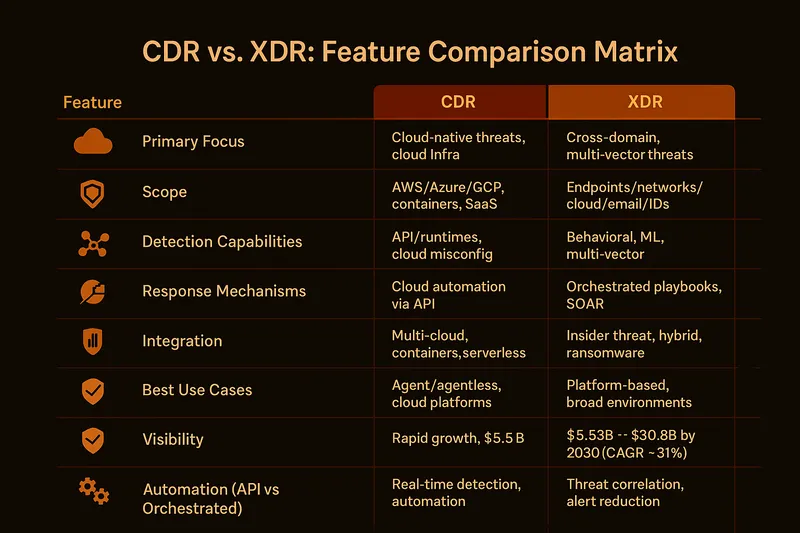
CDR vs XDR: Key Differences Explained
While both CDR and XDR aim to enhance threat detection and response capabilities, they differ significantly in scope, focus, and application. Understanding these distinctions is crucial for selecting the right solution for your organization.
Scope and Focus
| CDR: Cloud-Centric Security | XDR: Cross-Domain Integration |
|---|---|
| 1. CDR zeros in on cloud setups with custom detection for cloud-born threats. 2. It locks down workloads, services, and infra on AWS, Azure, GCP, and beyond. 3. Handles tricky bits like short-lived jobs, containers, serverless, and spread-out designs. | 1. Broad scope: unifies data from endpoints, networks, cloud workloads, email, identity, and apps. 2. One pane of glass across on‑prem, cloud, and hybrid estates. 3. Cross‑domain visibility surfaces patterns siloed tools miss. |
Detection Capabilities
| CDR Detection Methods | XDR Detection Methods |
|---|---|
| 1. CDR taps cloud APIs, runtime guards, and behavior scans fit for cloud-style attacks. 2. It catches IAM role climbs, sloppy S3 buckets, rogue API hits, and container jailbreaks. 3. Shines at nabbing threats from cloud quirks and setup flaws. | 1. XDR taps advanced analytics and ML for spotting threats over various attack layers. 2. Links signals from endpoints, networks, clouds, emails, and IDs to shrink blind spots. 3. Uncovers tricky moves like lateral shifts, living-off-land tricks, and multi-angle hits. |
Response Mechanisms
| CDR Automated Response | XDR Automated Response |
|---|---|
| 1. CDR hooks into cloud APIs for seamless, built-in response tools. 2. Auto-steps like locking workloads, tweaking security groups, pulling IAM rights, or splitting VPCs. 3. Rebuilds from trusted images fast, suiting cloud’s flexible, code-driven nature. | 1. XDR syncs responses across tools and layers for smooth threat handling. 2. Auto-moves cover isolating endpoints, blocking bad IPs, freezing accounts, and quarantining emails. 3. Ties in SOAR playbooks to lock down threats across the full security setup. |
Integration and Architecture
| CDR Integration | XDR Integration |
|---|---|
| 1. CDR meshes with AWS Security Hub, Azure Defender, GCP Security Command Center, and cloud SIEMs for smooth ops. 2. Runs agent-based on workloads or agentless via scans for flexible setups. 3. Pairs with CNAPP tools for upfront security checks before launch. | 1. XDR links up with EDR, NDR, SIEM, SOAR, firewalls, and email guards in your current setup. 2. Native versions from one maker blend parts seamlessly. 3. Open ones pull in outside tools via APIs for flexible fits. |
Use Cases and Applications
When CDR Shines
CDR is ideal for organizations with significant cloud footprints that need specialized protection for cloud-native architectures. It’s particularly effective for:
- Securing multi-cloud deployments (AWS, Azure, GCP)
- Protecting containerized applications and Kubernetes clusters
- Monitoring serverless and microservices architectures
- Detecting cloud-specific threats like crypto-mining and data exfiltration
- Ensuring cloud compliance and configuration security
When XDR Excels
XDR is best suited for organizations needing comprehensive security across diverse environments. It’s particularly valuable for:
- Hybrid IT environments with both on-premises and cloud infrastructure
- Organizations struggling with alert fatigue from multiple security tools
- Detecting sophisticated, multi-stage attacks across different vectors
- Security operations centers (SOCs) seeking operational efficiency
- Enterprises with complex security stacks requiring unified management
Deployment Complexity
| CDR Deployment Considerations | XDR Deployment Considerations |
|---|---|
| CDR deployment can face challenges including agent deployment complexity across dynamic cloud environments, potential performance impacts on workloads, coverage gaps in SaaS applications, and the need for cloud-specific expertise. However, agentless CDR solutions can simplify deployment by leveraging cloud APIs without requiring agent installation. | XDR implementation complexity stems from integrating disparate security tools, ensuring data quality across multiple sources, managing log retention requirements, and addressing compatibility issues between legacy systems and the XDR platform. Organizations need skilled personnel to configure, tune, and operate XDR effectively. |
Must for Read: Cloud-Native Application Protection Platforms (CNAPP): The Ultimate Guide for 2025
Comparison Table: CDR vs XDR
| Feature | CDR (Cloud Detection and Response) | XDR (Extended Detection and Response) |
|---|---|---|
| Primary Focus | Cloud environments (IaaS, PaaS, SaaS, containers) | Multiple security domains (endpoint, network, cloud, email, identity) |
| Scope | Cloud-specific threats and behaviors | Cross-domain threat correlation |
| Detection | Cloud-native threat patterns, misconfigurations, API abuse | Multi-vector attacks, behavioral anomalies |
| Response | Cloud-native automation via APIs (quarantine, rebuild, isolate) | Cross-platform orchestration (isolate, block, disable) |
| Best For | Organizations with significant cloud presence | Hybrid environments with diverse attack surfaces |
| Integration | Cloud provider platforms (AWS, Azure, GCP) | Broad security stack (EDR, SIEM, SOAR, firewalls) |
| Deployment | Agent-based or agentless in cloud | Platform-based across multiple environments |
| Visibility | Deep cloud infrastructure visibility | Broad cross-domain visibility |
| Use Cases | Multi-cloud security, container protection, serverless monitoring | Multi-stage attacks, insider threats, hybrid security |
| Market Size (2024) | Rapid growth, emerging market | $5.53 billion |
When to Use CDR vs XDR
Selecting between CDR and XDR—or implementing both—depends on your organization’s specific security requirements, infrastructure composition, and threat landscape.
Choose CDR When
- Your Infrastructure Is Predominantly Cloud-Based
- If your organization has migrated most workloads to cloud platforms like AWS, Azure, or Google Cloud, CDR provides the specialized protection needed for cloud-native architectures.
- Organizations running containerized applications, Kubernetes clusters, or serverless functions benefit most from CDR’s cloud-specific capabilities.
- Cloud-Native Threats Are Your Primary Concern
- When facing threats like cloud misconfiguration exploitation, IAM privilege escalation, unauthorized API access, data exfiltration from cloud storage, or crypto-mining attacks, CDR’s specialized detection logic identifies these cloud-specific attack patterns more effectively than general-purpose solutions.
- You Need Deep Cloud Visibility
- CDR excels when you require comprehensive visibility into cloud control plane activities, container runtime behaviors, serverless function executions, cloud service configurations, and multi-cloud resource interactions.
- Compliance Is Cloud-Focused
- Organizations subject to cloud-specific compliance requirements benefit from CDR’s continuous configuration monitoring, automated compliance reporting, and cloud-centric audit capabilities.
Choose XDR When
- You Operate a Hybrid Infrastructure
- XDR is ideal for organizations with mixed environments combining on-premises data centers, cloud workloads, and SaaS applications. Its cross-domain correlation bridges visibility gaps between different infrastructure types.
- Alert Fatigue Is Overwhelming Your SOC
- If your security team drowns in alerts from multiple disparate security tools, XDR consolidates and correlates alerts to surface high-priority threats while filtering noise. Studies show XDR significantly reduces the time security professionals spend on low-fidelity alerts.
- You Face Sophisticated Multi-Vector Attacks
- XDR shines when detecting complex attack chains that span multiple domains—for example, a phishing email leading to endpoint compromise, followed by credential theft, lateral movement across the network, and data exfiltration to cloud storage.
- You Want to Maximize Existing Security Investments
- Organizations with substantial investments in EDR, firewalls, SIEM, and other security tools can leverage XDR to unify these disparate solutions without replacing them entirely. Open XDR platforms integrate third-party tools to provide centralized visibility and management.
- SOC Efficiency Is a Priority
- XDR improves operational efficiency by automating investigation workflows, providing guided response actions, reducing mean time to detect and respond (MTTD/MTTR), and enabling threat hunters to work more effectively.
Also Read: Secure Cloud Architecture Design: Principles & Patterns; Best Practices
Can CDR and XDR Work Together?
Absolutely. In fact, many security-mature organizations implement both CDR and XDR in a complementary architecture. This layered approach provides:
- Comprehensive Coverage: CDR delivers deep cloud-specific protection while XDR provides broad cross-domain visibility
- Enhanced Detection: CDR’s specialized cloud threat intelligence feeds into XDR’s correlation engine, enabling detection of attack chains that traverse from on-premises to cloud
- Unified Response: XDR can orchestrate responses that include CDR’s cloud-native actions as part of broader incident response workflows
- Best-of-Breed Strategy: Organizations leverage CDR’s cloud expertise while maintaining XDR’s enterprise-wide coordination
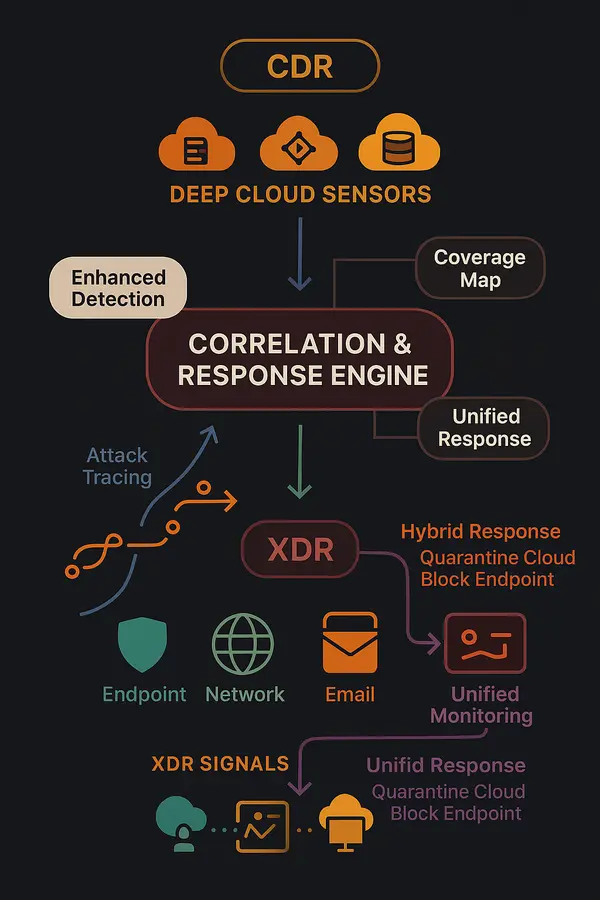
This integration ensures that cloud environments receive specialized protection while maintaining visibility into how cloud attacks relate to broader security incidents across the organization.
Implementation Considerations
Successfully deploying CDR or XDR requires careful planning, proper integration, and ongoing optimization. Here are key considerations for implementation:
Deployment Best Practices
For CDR Implementation
- Enable Comprehensive Logging: Activate and centralize logs from all cloud services and layers before deploying CDR
- Establish Cloud Baselines: Define normal behavior patterns for your cloud environment to improve anomaly detection accuracy
- Adopt Zero-Trust Principles: Implement continuous identity validation and least-privilege access to complement CDR capabilities
- Develop Cloud-Specific Incident Response Plans: Create playbooks that address the ephemeral and distributed nature of cloud environments
- Start with High-Value Assets: Prioritize CDR deployment for cloud workloads containing sensitive data or critical business functions
For XDR Implementation
- Assess Integration Capabilities: Evaluate how well the XDR platform integrates with your existing security stack
- Ensure Data Quality: Implement data normalization and quality controls to maximize XDR effectiveness
- Plan for Scalability: Select cloud-native XDR platforms that can dynamically adapt to organizational growth
- Define Clear Use Cases: Identify specific security challenges (alert fatigue, insider threats, ransomware) that XDR should address
- Pilot Before Full Deployment: Run proof-of-concept testing to validate real-world performance
Integration with Existing Security Stack
CDR Integration Approach
CDR should integrate seamlessly with your existing cloud security tools:
- CSPM (Cloud Security Posture Management): CDR complements CSPM by adding runtime threat detection to configuration monitoring
- CNAPP: Many modern CDR solutions are components of broader CNAPP platforms that span code-to-cloud security
- SIEM: CDR feeds cloud telemetry and security events into SIEM for centralized log management and correlation
- SOAR: Integrate CDR with SOAR platforms to automate complex response workflows
XDR Integration Approach
XDR serves as the unifying layer across your security ecosystem:
- EDR/NDR Integration: XDR extends endpoint and network detection by adding cloud, email, and identity data
- SIEM Enhancement: XDR provides real-time analytics that complement SIEM’s historical log analysis
- SOAR Orchestration: SOAR platforms can orchestrate XDR responses across the entire security infrastructure
- Threat Intelligence Feeds: Integrate external threat intelligence to enhance XDR detection accuracy
Skill Requirements
CDR Expertise Needed
- Cloud architecture and administration (AWS, Azure, GCP)
- Container and Kubernetes security
- Cloud-native application understanding
- Cloud IAM and identity management
- Incident response in cloud environments
XDR Expertise Needed
- Cross-domain security architecture
- Threat hunting and investigation
- Security tool integration and orchestration
- Data analysis and correlation
- Incident response across multiple domains
Organizations lacking internal expertise should consider managed detection and response (MDR) services that include CDR or XDR capabilities.
Also Read: Cloud Security Architecture (2025): Frameworks, Layers & Reference Diagram
Cost Considerations
CDR Investment Factors
- Licensing models (per workload, per user, per data volume)
- Agent deployment and maintenance costs (for agent-based solutions)
- Cloud API usage costs
- Integration expenses with existing cloud security tools
- Training and skill development
XDR Investment Factors
- Platform licensing (often priced per endpoint or user)
- Integration costs with existing security tools
- Data ingestion and storage expenses
- Professional services for implementation
- Ongoing managed services (if applicable)
ROI Considerations
Both CDR and XDR deliver measurable returns:
- Reduced incident response time (20% decrease in MTTR is common)
- Fewer security incidents requiring manual investigation (25-60% reduction)
- Avoided breach costs through faster detection
- Operational efficiency from automation (freeing 50% of security staff for higher-value work)
- Improved compliance posture reducing regulatory fines
The Future of CDR and XDR
The security landscape continues evolving rapidly, with both CDR and XDR technologies advancing to meet emerging threats and leverage new capabilities.
Market Growth and Trends
CDR Market Trajectory
The Cloud Detection and Response market is experiencing explosive growth driven by accelerating cloud migration and increasingly sophisticated cloud-targeted attacks. Organizations recognize that legacy security solutions cannot effectively address the dynamic nature of cloud threats, fueling significant investment in specialized CDR technologies.
Key CDR trends include:
- Shift towards cloud-native security over retrofitted on-premises tools
- Growing integration with CNAPP platforms for code-to-cloud protection
- Emphasis on serverless and container security capabilities
- Increased focus on multi-cloud unified detection and response
XDR Market Explosion
The XDR market is witnessing remarkable expansion, valued at $5.53 billion in 2024 and projected to reach $30.86 billion by 2030, representing a 31.2% compound annual growth rate. This growth is driven by increasing cyberattacks, regulatory compliance requirements, and the integration of security tools alongside cloud technology adoption.
Regional highlights include:
- Asia Pacific leading growth as enterprises modernize security infrastructure
- Large enterprises dominating adoption due to complex multi-geography environments
- Retail, e-commerce, and financial services sectors showing highest growth rates
AI and Machine Learning Integration
Both CDR and XDR are rapidly incorporating artificial intelligence and machine learning capabilities to enhance threat detection and response.
AI-Powered Threat Detection
Modern CDR and XDR solutions leverage AI to:
- Analyze vast amounts of data in real-time to identify patterns and anomalies
- Reduce false positives through contextual analysis and correlation
- Predict and preempt threats by identifying early-stage attack indicators
- Continuously learn from new threats to improve detection accuracy
- Automate threat prioritization based on risk and potential impact
You can Also Read: Context-Based Prioritization for CSPM: Fix What Actually Reduces Risk
Machine Learning Applications
ML algorithms enhance CDR and XDR through:
- Behavioral Analytics: Establishing baseline behaviors and flagging deviations that indicate threats
- Anomaly Detection: Identifying unusual activities across cloud resources or security domains
- Pattern Recognition: Detecting sophisticated attack chains across multiple vectors
- Automated Response: Optimizing response strategies through reinforcement learning
- Threat Intelligence: Processing global threat data to identify emerging attack methods
Emerging Capabilities
CDR Evolution
CDR solutions are advancing to address next-generation cloud security challenges:
- Deep Learning for Cloud Workload Protection: Enhanced detection of zero-day exploits and advanced persistent threats in cloud environments
- Automated Threat Hunting: AI-driven proactive threat hunting across multi-cloud infrastructures
- Cloud-Native SOAR Integration: Seamless orchestration between CDR detection and automated response playbooks
- DevSecOps Integration: Embedding CDR insights into CI/CD pipelines for shift-left security
XDR Innovation
XDR platforms are expanding capabilities to provide even more comprehensive protection:
- Native AI Assistants: Conversational AI interfaces for natural language threat investigation
- Unified SIEM/XDR Platforms: Convergence of SIEM and XDR into single platforms combining log management and active response
- Extended Coverage: Including OT/IoT environments, 5G networks, and edge computing in XDR scope
- Predictive Analytics: Using AI to anticipate and prevent attacks before they occur
The future of both technologies points toward increased automation, deeper AI integration, and more seamless orchestration across security tools—all aimed at helping security teams stay ahead of increasingly sophisticated threat actors.
Also Read: Cloud Security Best Practices for 2025
Conclusion
The CDR vs XDR comparison ultimately comes down to your organization’s specific security requirements and infrastructure composition. CDR provides specialized, cloud-native protection tailored for organizations with significant cloud footprints, offering deep visibility into cloud workloads, containers, and serverless architectures. XDR delivers comprehensive, cross-domain threat detection and response across endpoints, networks, cloud, email, and identity systems—ideal for hybrid environments and organizations seeking to unify disparate security tools.
Key takeaways for your decision:
- Choose CDR if your infrastructure is predominantly cloud-based and you face cloud-specific threats requiring specialized detection capabilities
- Choose XDR if you operate hybrid environments, struggle with alert fatigue, or need to detect sophisticated multi-vector attacks
- Implement both for comprehensive protection combining cloud-specific expertise with enterprise-wide visibility
The security landscape will continue evolving, with both CDR and XDR incorporating advanced AI capabilities, expanding coverage, and delivering increasingly automated threat detection and response. Organizations that invest in the right solution—or strategic combination of both—position themselves to defend effectively against today’s threats while preparing for tomorrow’s challenges.
Ready to strengthen your cloud security posture?
Assess your current infrastructure, identify your primary threat vectors, and evaluate whether CDR’s cloud-native specialization, XDR’s cross-domain integration, or a combined approach best serves your organization’s security objectives. The right detection and response strategy is not just a technology decision—it’s a business imperative in an era of escalating cyber threats.
About Cy5
Cy5 provides comprehensive cloud security solutions including Cloud Detection and Response (CDR), Cloud Security Posture Management (CSPM), and Cloud Infrastructure Entitlement Management (CIEM) to help organizations secure their cloud infrastructure across AWS, Azure, and Google Cloud Platform. Learn how Cy5 can enhance your cloud security strategy and protect your critical cloud workloads from advanced threats.





