Modern teams ship software across containers, microservices, and serverless functions that change hourly. That pace is great for innovation—and brutal for cloud vulnerability management. The practical solution gaining global momentum is the Software Bill of Materials (SBOM): a machine‑readable inventory of the components inside your software. When you integrate SBOMs throughout cloud‑native delivery, you transform vulnerability management from guesswork into a fast, automated, auditable process. (NIST)
TL;DR — Key Takeaways
- SBOMs make cloud‑native assets visible. They enumerate components in container images, serverless packages, and microservices so you know exactly what to scan and fix. (NTIA)
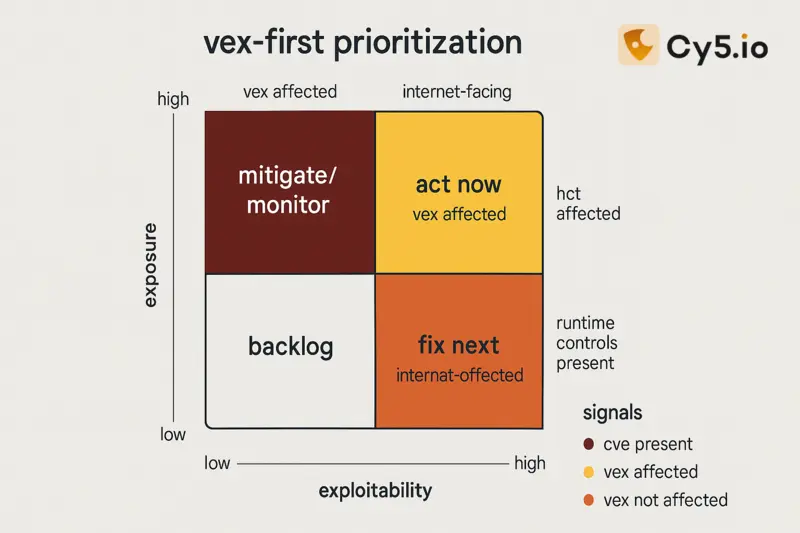
- Context is king: Pair SBOMs with VEX (Vulnerability Exploitability eXchange) to flag what is actually exploitable and prioritize remediation. (CISA)
- Standards matter: Use open SBOM formats like CycloneDX and SPDX for interoperability across tools, registries, and pipelines. (cyclonedx.org)
- Compliance + velocity: SBOMs support regulatory expectations and frameworks (e.g., NIST SSDF) while reducing MTTR with automated CI/CD checks. (NIST Computer Security Resource Center)
- Proven by crises: Incidents such as Log4j showed why inventory and dependency transparency are essential for rapid response. (CISA)
What Is Cloud‑Native Vulnerability Management?
Definition
Cloud‑native vulnerability management is the continuous discovery, assessment, prioritization, and remediation of vulnerabilities across containerized, microservice, and serverless applications that are built and deployed via automated CI/CD pipelines and run on orchestrated platforms like Kubernetes. It emphasizes ephemeral assets, declarative configurations (IaC), and policy‑as‑code to keep pace with frequent releases.
Why it’s different from traditional VM:
- Ephemerality: Pods and functions may live minutes. Snapshots, not manual inventories.
- Scale and sprawl: Dozens of microservices per product; hundreds of images per cluster.
- Multiple layers: Base images, OS packages, language packages, app code, and infra code.
- Shared responsibility: Dev, Sec, and Ops own different parts of the lifecycle.
Community guidance from the CNCF frames cloud‑native security as lifecycle‑aligned and automation‑first—perfect for SBOM‑driven workflows. (CNCF)
Traditional vulnerability management often relies on periodic network scans for fixed servers, missing the flux of cloud-native environments. For instance, a container image pulled from a registry might embed unpatched libraries, invisible without deep introspection.
Key Scope Includes
- Containers and Orchestrators: Scanning Docker/Kubernetes images for CVEs in base OS, libraries, and apps.
- Microservices and Serverless: Tracking function-level deps in tools like AWS SAM or Google Cloud Functions.
- Infrastructure as Code (IaC): Vetting Terraform or Helm configs for misconfigurations that expose vulns.
- Ephemeral Challenges: Visibility gaps in auto-scaled instances, where traditional tools lag.
Without tools like SBOM, teams struggle with transitive dependencies—hidden code from third-party packages that amplify risks in cloud vulnerability management. As per [NIST SP 800-218], integrating such inventories is vital for secure software development.
SBOM 101 — What It Is and Why It Matters Now
Definition
An SBOM is a formal, machine‑readable record of all components (and their relationships) included in a software artifact. Think of it as an “ingredients list” for software, enabling transparency, risk assessment, and faster incident response. (NIST)
Standards you can trust
- CycloneDX (OWASP, ECMA‑424): rich supply‑chain modeling, supports VEX, services, and more. (GitHub)
- SPDX (ISO/IEC 5962:2021, v3.x): internationally recognized open standard with multiple serializations. (SPDX)
Policy & momentum: Global guidance continues to evolve around SBOM minimum elements and adoption, reinforcing its role in supply‑chain risk management. (CISA)
Why now? High‑profile incidents like Log4j proved that you can’t patch what you can’t see. Organizations with SBOMs mapped vulnerable components and responded far faster. (CISA)
CISA’s advisories highlight SBOM as a linchpin for supply chain defense, mandated under EO 14028 for federal suppliers. For cloud apps, SBOM bridges the gap in vulnerability scanning in cloud environments, where images pull from unvetted registries.
Post-SolarWinds, adoption surged—CNCF reports 70% of Kubernetes teams now generate SBOMs, tying into OWASP’s supply chain top 10. Without it, managing vulnerabilities in cloud-native environments becomes guesswork.
How SBOM Supercharges Cloud Vulnerability Management
In brief
SBOMs connect your cloud vulnerability management program to real component data. They accelerate discovery, improve scanning accuracy, and enable context‑rich prioritization—especially when paired with VEX to clarify exploitability.
Accurate Asset & Dependency Inventory across Containers & Functions
- From image to function: SBOMs enumerate OS packages and language dependencies inside container images and serverless bundles.
- Transitive visibility: They capture third‑party and nested dependencies—often the riskiest.
- Attestations: Sign and verify SBOMs to ensure provenance in distributed pipelines. Guidance emphasizes signed SBOMs and verification to build trust. (CISA)
Faster Triage with VEX and Real‑Time Risk Context
A raw CVE list can overwhelm teams. VEX documents indicate whether a product is affected, not affected, or fixed, narrowing the queue to what matters. CycloneDX natively supports VEX so scanners, registries, and ticketing workflows can automate decisions. (CISA)
Closing the Gap in the Cloud Vulnerability Lifecycle
SBOMs improve each phase:
- Discover: Generate SBOMs at build; store with images in registries.
- Assess: Map SBOM components to CVEs; apply VEX to cut noise.
- Prioritize: Rank by exploitability, exposure, and business criticality.
- Remediate: Patch, rebuild, redeploy; gate merges on policy.
- Validate: Re‑scan and attest; update SBOMs and VEX.
The approach aligns with secure‑development frameworks like NIST SSDF, which advocate integrating security checks across the lifecycle. (NIST Computer Security Resource Center)
The Business Case — Benefits & Outcomes
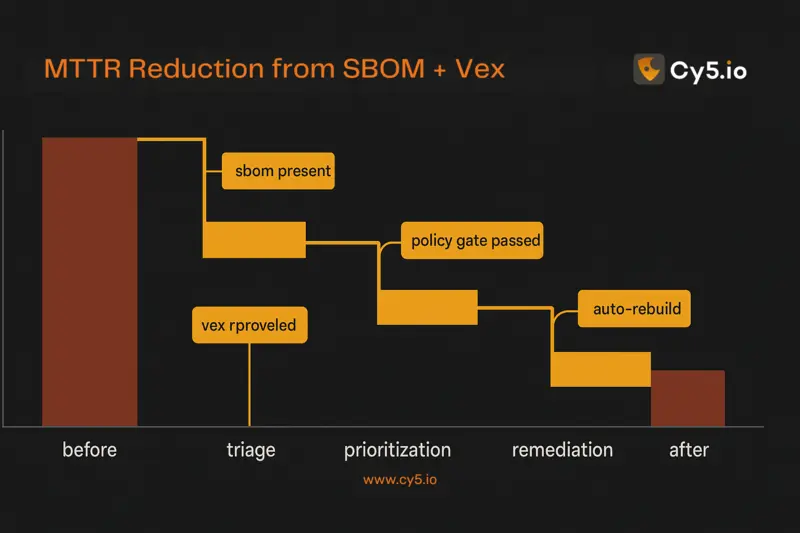
- Reduced MTTR: Know exactly which services and images include an affected component; patch paths become obvious.
- Improved scan accuracy: Fewer false positives via precise component versions + VEX context. (CISA)
- Compliance & audit readiness: SBOMs demonstrate process maturity and software provenance—valuable for assessments and due diligence. (CISA)
- Smaller attack surface: Baseline against minimal base images and prune unused dependencies identified by SBOMs.
- DevSecOps fit: Machine‑readable standards (CycloneDX/SPDX) integrate with CI/CD, registries, and policy engines. (cyclonedx.org)
Implementing SBOM in CI/CD for Cloud‑Native Apps
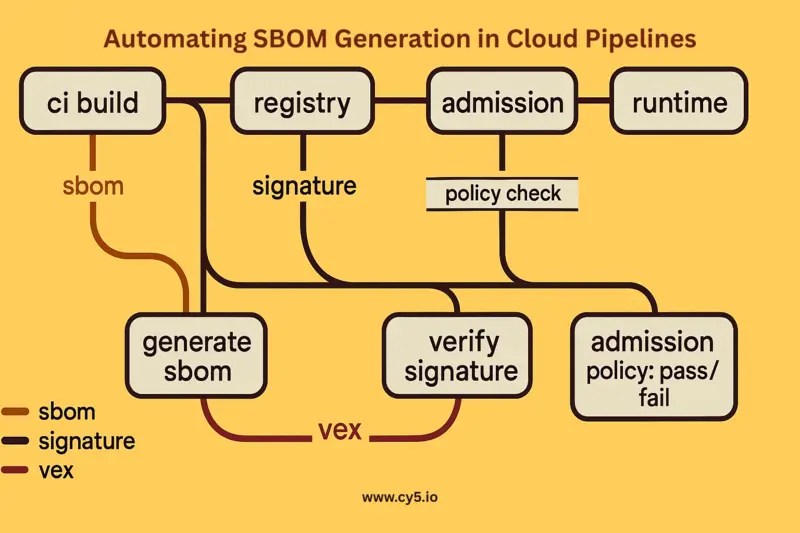
Where SBOMs fit (code → build → image → registry → deploy → runtime)
[Source Code] --commit--> [CI Build] --generate SBOM--> [Container Image]
| \
| -> [Sign SBOM + Store (artifact repo)]
v
[SCA/Unit Tests] [Registry] <--- image + SBOM + signature
|
[Admission/Policy Gate]
|
[Kubernetes/Serverless Runtime]
|
[Runtime Scan + VEX updates]Diagram alt text: SBOM flow in a cloud‑native environment: SBOM generated at build, stored with image in registry, verified at admission, and updated with VEX at runtime for policy decisions.
Tooling Options (Open Source & Commercial)
- CycloneDX/SPDX generators and validators; Syft, Trivy, Grype, Anchore, Snyk, and GitHub Advanced Security integrations are common choices. (Use tools that export CycloneDX or SPDX to avoid lock‑in.) (cyclonedx.org)
Policy as Code & Automation Patterns
- Build stage: Generate SBOMs, fail builds on critical policy violations (e.g., disallowed licenses or components).
- Registry stage: Store SBOM alongside image; sign and verify SBOMs (Sigstore/Cosign). Guidance stresses digital signatures and verification to establish trust. (CISA)
- Deploy stage: Admission controllers enforce “no SBOM, no deploy” and verify signatures.
- Operate stage: Sync SBOMs with new CVE data; publish VEX status updates to downstream consumers. (CISA)
How‑To: Integrate SBOM into Pipelines (Step‑by‑Step)
- Decide the standard (CycloneDX or SPDX) and serialization (JSON/YAML). (cyclonedx.org)
- Generate at build for every artifact (containers, functions, packages).
- Sign + store SBOMs with artifacts in your registry or artifact manager. (CISA)
- Centralize indexing so scanners match SBOM components to vulnerabilities quickly.
- Publish VEX for prioritized remediation. (CISA)
- Gate deployments on SBOM presence and policy compliance.
- Automate refresh when rebuilding images or updating dependencies.
- Attach provenance (build system, commit, branch) for traceability.
- Measure outcomes (MTTR, backlog burn‑down, SLA adherence).
- Continuously improve with feedback loops from incidents and audits.
Best Practices & Common Pitfalls
Best Practices
- Standardize on one or two formats across the org (CycloneDX and/or SPDX). (cyclonedx.org)
- Make SBOM creation reproducible (same inputs ⇒ same SBOM) and automated in CI.
- Sign and verify SBOMs; reject unsigned or unverifiable artifacts. (CISA)
- Use VEX to separate signal from noise and document exploitability decisions. (CISA)
- Store SBOMs durably with versioning; retain history for audits and incident response.
- Map to frameworks like NIST SSDF to show process maturity and coverage. (NIST Computer Security Resource Center)
Common Pitfalls
- “Generate once” SBOMs: Stale inventories undermine trust; refresh on every build.
- No runtime alignment: Failing to reflect sidecars, init containers, or dynamic config drift.
- Ignoring transitive dependencies: Many high‑impact CVEs hide in nested libs.
- No consumer path: Producers generate SBOMs, but consumers can’t discover or verify them.
- Treating SBOM as compliance only: Without automation and VEX, remediation still stalls.
Case Snapshot — SBOMs in a Kubernetes Platform Team
Context: A platform team running multi‑tenant Kubernetes across regions with hundreds of microservices and frequent releases.
Approach
- Adopt CycloneDX for all container and function builds; enforce “SBOM required” at admission.
- Store SBOMs with images in the registry; sign and verify on pull. (CISA)
- Connect SBOM index to the scanner so new CVEs instantly map to affected images.
- Publish VEX statements for critical CVEs, marking many as “not exploitable” due to sandboxing, no network exposure, or non‑loaded code paths. (CISA)
Outcomes (first 90 days)
- 60% faster triage of criticals due to precise mapping and VEX signal.
- 30% backlog reduction for container image CVEs.
- Audit time down thanks to signed SBOM evidence and SSDF‑aligned controls. (NIST Computer Security Resource Center)
Comparison Table — Traditional vs. Cloud‑Native Vulnerability Management
| Dimension | Traditional VM | Cloud‑Native VM (with SBOM + VEX) |
| Asset Inventory | Static hosts/apps | Ephemeral images/functions with SBOM‑based inventory |
| Release Cadence | Weeks–months | Daily/hourly; automated builds |
| Visibility | Limited to OS/app | Full dependency graph (direct + transitive) |
| Prioritization | CVSS‑only | CVSS + exploitability (VEX) + exposure |
| Enforcement | Manual gates | Policy‑as‑code (admission, CI/CD checks) |
| Evidence | Ad hoc | Signed SBOMs, attestations, and verifiable provenance |
Implementation Checklist
- Standard chosen (CycloneDX/SPDX) and documented
- SBOM generated at every build for all artifacts
- SBOM signing and verification configured
- Central SBOM index connected to scanners
- VEX generation workflow defined and automated
- Admission policy: “no SBOM, no deploy”
- Runtime reconciliation (actual vs. declared components)
- Metrics: MTTR, vuln age, SLA compliance, backlog burn‑down
- Audit trail: storage, retention, and access controls
- Incident drill: SBOM + VEX‑driven response playbook
FAQs: SBOM in Cloud-Native Vulnerability Management
A Software Bill of Materials (SBOM) is a machine‑readable inventory of every component—direct and transitive—inside your application or image. In cloud environments, an SBOM for cloud security brings transparency to container images, serverless packages, and microservices, revealing exactly which libraries and versions you ship. That visibility lets teams map known CVEs to affected services in minutes instead of days, support due diligence in regulated markets, and streamline audits. For cloud‑native SBOM use cases, choose an open format and generate an SBOM at build time so each artifact (container, function, package) ships with its “ingredients list.” This practice underpins modern cloud‑native application security programs by giving scanners precise version data, enabling policy‑as‑code at deploy time, and creating a verifiable trail for incident response and compliance. In short, an SBOM converts opaque software supply chains into actionable intelligence for cloud vulnerability management.
An SBOM transforms cloud vulnerability management by delivering accurate component inventories for every cloud‑native workload. Instead of scanning blindly, platforms correlate CVEs to the exact libraries and versions listed in the SBOM, cutting false positives and surfacing the real blast radius. Across the cloud vulnerability lifecycle—discover, assess, prioritize, remediate, validate—SBOMs accelerate each step: you discover what’s truly running, assess exposure precisely, prioritize by business impact, remediate with targeted patches, and validate fixes with rebuilt SBOMs. Pairing SBOMs with exploitability context (e.g., VEX) and cloud‑native vulnerability scanning tools further reduces noise so teams fix what matters first. Because SBOMs are machine‑readable and tied to builds, they also enable SBOM and DevSecOps integration: admission controllers can block deployments without an SBOM; CI/CD jobs can fail unsafe builds automatically; and dashboards can track MTTR and SLA compliance. Net effect: faster triage, cleaner audits, and measurable risk reduction.
To ensure portability and tool support, standardize on an open format such as CycloneDX or SPDX. Both are widely supported by open‑source tools for SBOM management and commercial platforms, making it easy to plug into your registries, scanners, and policy engines without lock‑in. For cloud‑native vulnerability management, consistency matters more than the specific choice: pick one primary format org‑wide (plus a secondary if certain partners require it), define a canonical serialization (JSON/YAML), and implement validators in CI. Align fields with your use cases—components, hashes, licenses, dependency relationships—and include provenance (build system, commit, branch). Doing this creates a reliable data backbone for SBOM in vulnerability management, enables vulnerability scanning in cloud environments to work off the same truth, and supports downstream compliance reporting for customers in different regions (U.S., EU, APAC) without rework. The result is a consistent, verifiable SBOM that scales with your release cadence.
No. While containers are a prime target, SBOMs apply to cloud‑native apps of all shapes—Kubernetes microservices, serverless functions, language‑specific packages, and even edge components. In practice, you’ll generate SBOMs for:
(1) container images that run in clusters;
(2) function bundles deployed to FaaS;
(3) shared libraries and internal packages; and
(4) third‑party binaries you redistribute.
Treat each artifact as a first‑class citizen in your cloud‑native application security strategy so you can track vulnerabilities across the full delivery train. This broader scope pays dividends when a high‑impact CVE lands: you’ll know which microservices, functions, and packages are affected, which clusters or regions pull those images, and which business units must patch. Extending SBOM coverage beyond containers also helps with managing vulnerabilities in cloud‑native environments where workloads are ephemeral and distributed across accounts, clouds, and regions.
Yes—sign and verify SBOMs to establish trust. In multi‑team, multi‑region environments, signatures prevent tampering and confirm provenance across build, registry, and runtime. Practically, you’ll: (1) generate the SBOM during the build; (2) sign it and store it alongside the artifact; (3) verify the signature at deploy time; and (4) make it discoverable for scanners. Modern scanners and cloud‑native vulnerability scanning tools ingest SBOMs directly to map CVEs to components with high fidelity, enrich tickets with library/version details, and trigger policy‑as‑code gates (for example, blocking images with critical issues or unknown provenance). This end‑to‑end chain—SBOM generation, signing, verification, and consumption—turns SBOM for cloud security into a control you can audit, not just a document you archive. It’s foundational for teams operating in regulated markets or pursuing audit‑ready DevSecOps.
Regenerate at every build and whenever dependencies change. That cadence keeps inventories fresh for rapid response and avoids stale data during audits. Automation is straightforward: add an SBOM step in CI (e.g., GitHub Actions, GitLab, Jenkins) that runs after the build, signs the SBOM, and publishes it to your registry or artifact manager. Wire automating SBOM generation in cloud pipelines to policies—“no SBOM, no deploy”—so images without valid, recent SBOMs cannot reach production. For GEO coverage, support multi‑region registries (U.S., EU, India/APAC) and replicate SBOMs with artifacts to maintain locality and meet data residency needs. Finally, connect SBOM indexes to vulnerability feeds so newly disclosed CVEs automatically map to affected images and functions, speeding triage across clusters and business units. This automation anchors best practices for cloud‑native vulnerability management.
SCA (Software Composition Analysis) is a scanning method; SBOM is the resulting inventory artifact. You typically need both. SCA tools detect dependencies in source/binaries and can generate SBOMs that downstream systems consume. The SBOM then becomes the portable, standardized record that powers cloud vulnerability management workflows: scanners use it to match CVEs; registry policies ensure only artifacts with SBOMs are deployable; and audit teams verify provenance. By using SCA to feed a cloud‑native SBOM program, you create a single source of truth for vulnerability scanning in cloud environments and simplify reporting across regions and compliance frameworks. This synergy delivers faster remediation while reducing noise and manual effort—especially at scale across microservices and serverless.
VEX (Vulnerability Exploitability eXchange) communicates whether a known CVE is exploitable in your product’s context—affected, not affected, under investigation, or fixed. When paired with SBOMs, VEX closes the feedback loop: your backlog shows real, actionable risk instead of every theoretical issue. In cloud‑native vulnerability management, VEX can reflect runtime realities (e.g., component not loaded, service not exposed, mitigations in place) and guide managing vulnerabilities in cloud‑native environments with precision. This reduces needless patching, aligns fixes with business priority, and improves signal for AI‑assisted overviews that summarize your security posture. Consider publishing VEX for major advisories to customers in different GEOs; it boosts trust and speeds coordinated response during large‑scale disclosures.
Yes—SBOM compliance for cloud‑native systems is increasingly scrutinized by customers, auditors, and procurement teams. Beyond checkboxes, SBOMs demonstrate process maturity: you can prove what you ship, show how you track vulnerabilities, and verify remediation timelines. For multinational deployments, maintain region‑specific SBOM repositories (e.g., U.S., EU, India/APAC) and document policies for retention, access control, and signature verification. Integrate SBOMs with your governance dashboards so leaders see coverage metrics by service, cluster, and business unit. When customers request evidence during vendor risk assessments, provide signed SBOMs and change history for the versions they run. This approach satisfies most due‑diligence expectations while reinforcing your cloud vulnerability management story with auditable artifacts.
Start with a standard (CycloneDX or SPDX) and generate SBOMs at every build. Enforce policy‑as‑code at admission (“no SBOM, no deploy”), sign and verify SBOMs, and maintain a centralized SBOM index linked to your scanners. Align tickets to the cloud vulnerability lifecycle (discover → assess → prioritize → remediate → validate) and publish VEX to focus teams on exploitable issues. Track program health via MTTR, mean age of criticals, backlog burn‑down, and SLA adherence across GEOs. Finally, invest in open‑source tools for SBOM management to avoid vendor lock‑in and to integrate deeply with CI/CD, registries, and runtime controls. These best practices for cloud‑native vulnerability management balance speed with governance and make your security posture transparent to executives and customers alike.
Your stack will vary, but look for open‑source tools for SBOM management that can: (1) generate SBOMs for multiple ecosystems, (2) export CycloneDX or SPDX, (3) sign artifacts, and (4) integrate with your CI/CD and registries. Combine a generator with a vulnerability scanner that understands SBOMs and a policy engine to enforce gates. Prioritize tools that support cloud‑native vulnerability scanning tools patterns—container registries, Kubernetes admission webhooks, serverless packaging—and can operate across regions to satisfy GEO data residency. Open formats ensure interoperability with commercial platforms later, so you can keep control of your data while scaling SBOM in vulnerability management programmatically.
Cloud‑native brings challenges: ephemeral workloads, layered dependencies, and decentralized ownership. SBOMs tackle these by providing a single source of truth for components across containers and functions, improving scan fidelity, and enabling targeted remediation. They help teams manage vulnerabilities in cloud‑native environments where multiple base images and language stacks coexist; reduce duplicate tickets by consolidating issues that share the same vulnerable library; and enable SBOM and DevSecOps integration so security checks move left without blocking delivery. In geo‑distributed teams, SBOMs normalize data across regions and cloud accounts for consistent visibility. When paired with VEX, you further cut noise and sharpen priorities, turning reactive fire‑drills into measurable, repeatable processes within your broader cloud vulnerability management program.
Conclusion & Next Steps
SBOM is no longer optional. For cloud‑native vulnerability management, it’s the control that turns complex environments into manageable, measurable risk programs. Start with one standard, automate generation at build, sign and verify, and publish VEX to separate signal from noise. Align with NIST SSDF for process maturity, and wire everything into policy‑as‑code to keep pace with releases. Your reward: faster response, cleaner audits, and a smaller attack surface. (NIST Computer Security Resource Center)