Scan containers, serverless workloads, and cloud infrastructure for vulnerabilities. Visualize, prioritize, and remediate risks with our next-gen CNAPP platform.
Detection Accuracy
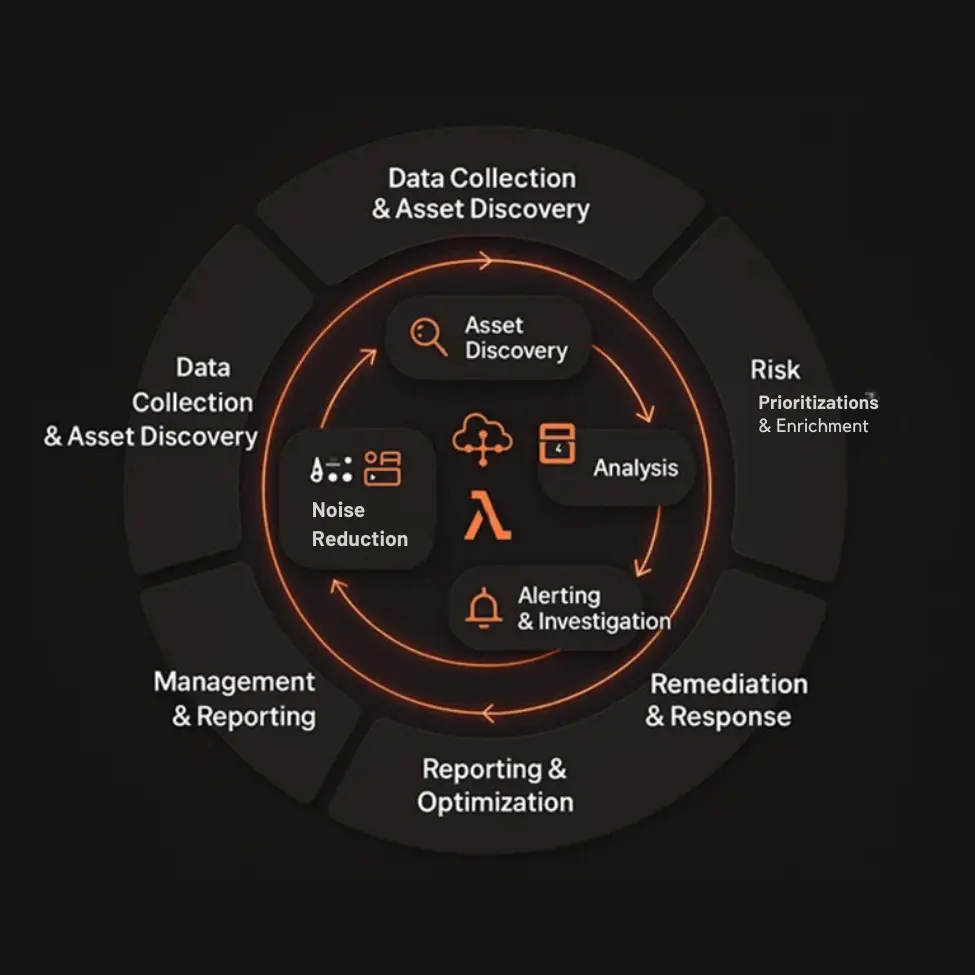








From container images to serverless functions, modern cloud environments are complex and dynamic. Without deep visibility and scanning, vulnerabilities can go undetected—leading to breaches, downtime, and compliance failures.
“Approximately 85% of organizations have reported experiencing at least one data breach in their cloud environment over the past year, indicating data breaches as a predominant threat.”
(Source: Adivi)
Solution
At Cy5, vulnerability management isn’t a tool—it’s a collaborative shield. We merge cutting-edge automation with human expertise to expose hidden risks across cloud-native environments, containers, and CI/CD pipelines. Our CNAPP-powered platform continuously maps your attack surface, prioritizes threats using exploitability and business context, and delivers actionable remediation playbooks—reducing mean-time-to-patch by 83%.
Transparency Note: This workflow reflects our shared accountability model: Cy5 provides scanning, prioritization, and expert guidance; clients implement fixes and maintain configurations. Together, we close gaps.
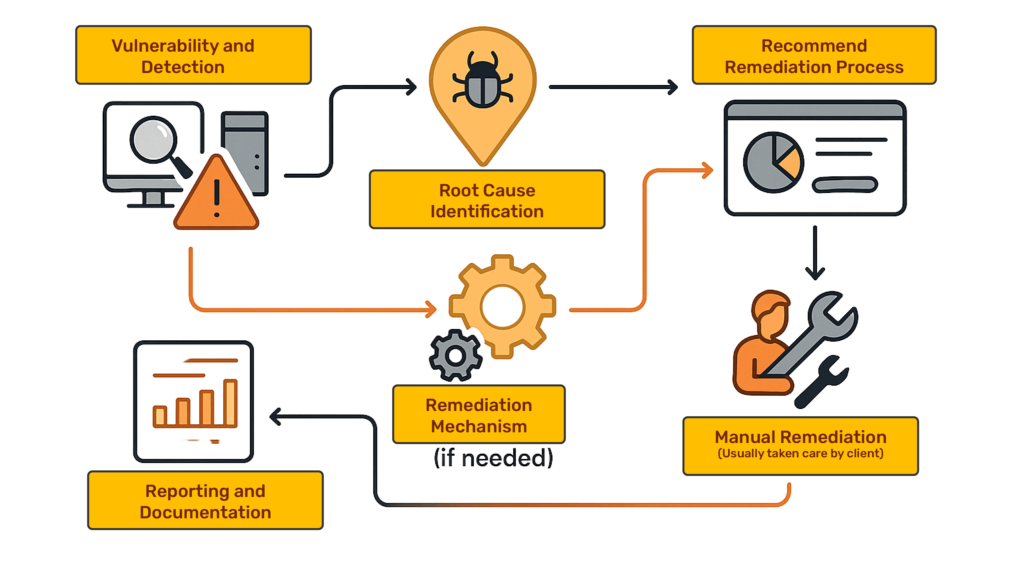
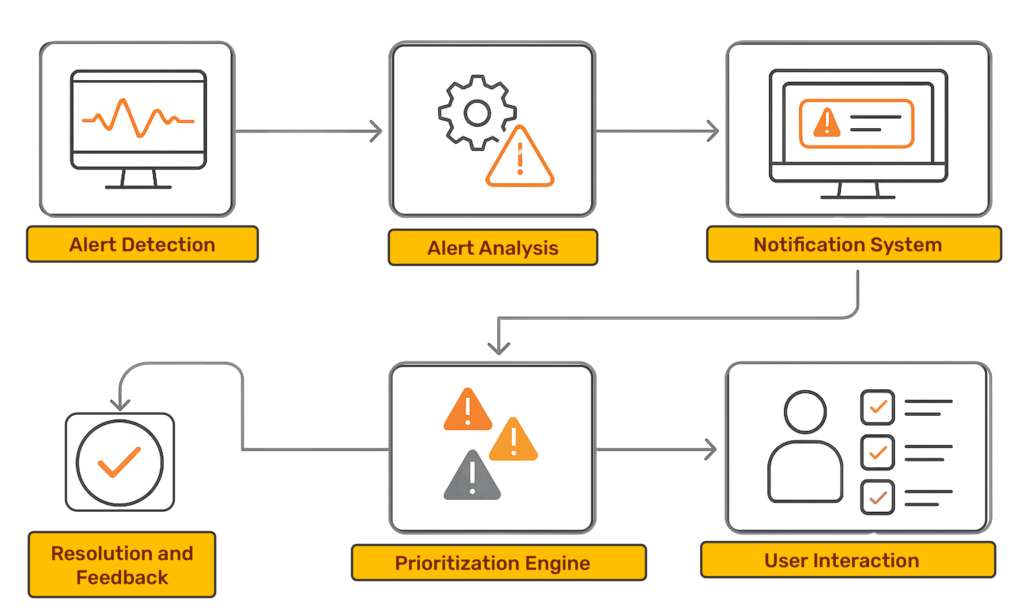
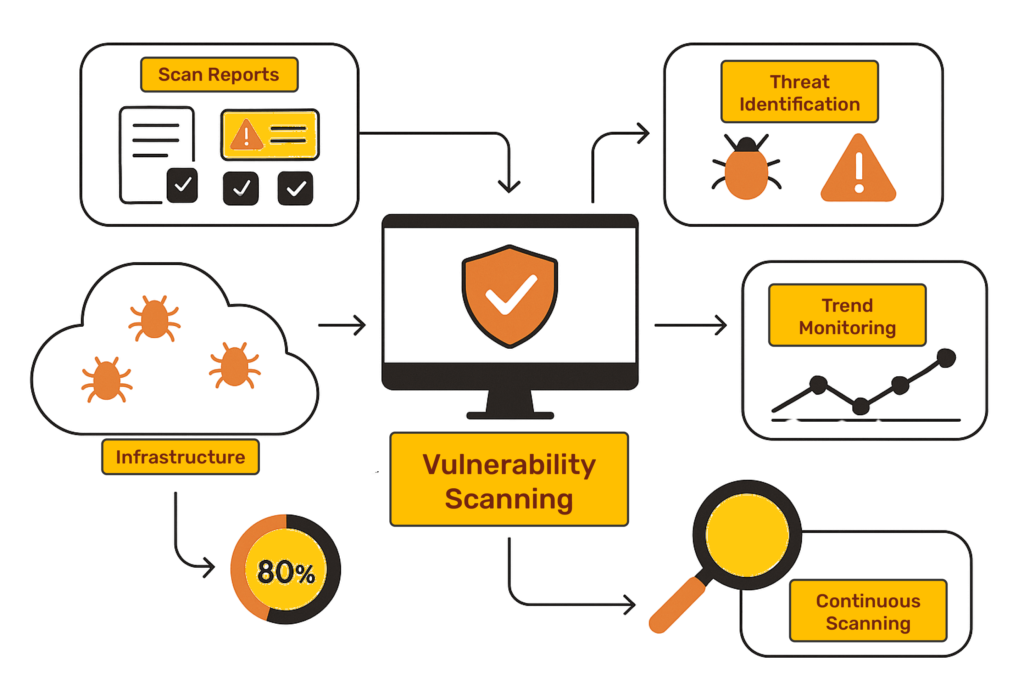
In cloud-native environments where threats evolve faster than traditional defenses, true security emerges from symbiotic partnership—not standalone tools. Cy5 redefines vulnerability management by merging context-based intelligence with crystal-clear accountability frameworks. Our approach transforms fragmented workflows into a unified security continuum
Cy5’s Role


Your Advantage
Our dashboards let you configure policies, schedule scans, and manage exceptions with point-and-click simplicity.
→ Outcome: Unified visibility into asset risks and compliance gaps.
→ Advantage: Reduce exposure without drowning in complexity.


We handle 24/7 vulnerability scanning and context-based risk scoring—you control remediation in your cloud environment.
→ Outcome: Faster threat response with full operational sovereignty.
→ Advantage: Align security with your workflows, not the other way around.
Get instant alerts + actionable remediation playbooks for critical gaps—backed by our proactive support team.
→ Outcome: Continuous resilience, even when human error occurs.
→ Advantage: Turn vulnerabilities into verified fixes, backed by expert guidance.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

Minimize your attack surface with proactive detection.

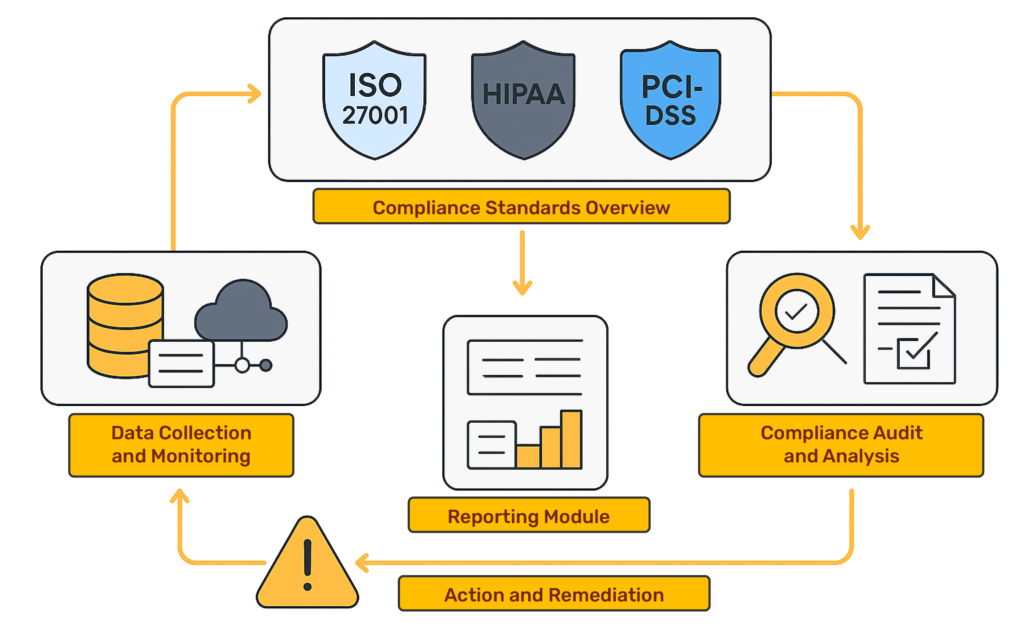
Generate audit-ready reports with a single click.

Automate manual processes and reduce remediation time.
From discovery to remediation in one integrated platform
Deploy lightweight agents or agentless scans across your network.
Identify vulnerabilities using the latest CVE databases and threat intelligence.
Apply patches or mitigation strategies with guided workflows.




Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Vulnerability management in cloud security is the continuous process of identifying, assessing, prioritizing, and remediating security weaknesses across cloud-native environments like containers, serverless functions, and virtual machines. It helps organizations reduce risk, maintain compliance, and protect cloud workloads from cyber threats.
SBOM (Software Bill of Materials) provides a detailed inventory of all software components and dependencies in an application. In vulnerability management, SBOM enables precise detection of known vulnerabilities (CVEs) in third-party libraries and packages, allowing teams to prioritize and remediate risks more effectively.
Best practices include continuous scanning of containers and serverless workloads, generating SBOMs for dependency visibility, prioritizing vulnerabilities using severity scores and metadata, integrating with CI/CD pipelines, and leveraging AI-powered remediation tools for faster response.
Yes, our platform supports scanning of publicly hosted container images from registries like Docker Hub and Amazon ECR. It identifies vulnerabilities, tags them with severity scores, and provides remediation guidance—all within a unified console.
Traditional vulnerability management tools are often designed for static, on-premise environments. In contrast, cloud vulnerability management must handle dynamic, ephemeral workloads like containers and serverless functions, requiring real-time scanning, SBOM analysis, and environment-aware prioritization.
Our platform uses a combined severity score based on CVSS ratings, exploitability, asset context, and environment tagging. This helps security teams focus on the most critical vulnerabilities across images, packages, and cloud environments.
Yes, AI-powered remediation is coming soon. It will provide intelligent suggestions and automated workflows to fix vulnerabilities faster, reducing manual effort and response time.
Absolutely. Vulnerability management is a core requirement in compliance standards like ISO 27001, SOC 2, PCI-DSS, and HIPAA. Our platform offers compliance-ready reports and dashboards to support audits and regulatory needs.