Cloud adoption is growing, at an ACCELERATED rate! The bad guys love the cloud too, since it’s where valuable data resides, and is often prone to misconfigurations or errors if it’s not dealt with properly. We’ll talk about 17 open source cloud security tools that have helped organisations globally over years. Here goes!
Cloud Security Scanning
Probably one of the most important aspects of public cloud security! It is extremely crucial to ensure security teams have visibility into cloud deployments as well as get notified of any misconfiguration that could lead to a potential security breach.
#1 Security Monkey
Use Case : Scanning for Cloud Misconfigurations
Details : Netflix has been very kind to the public cloud and cyber security community by releasing a series of open source projects. Security Monkey, is tool by Netflix that automates configuration reviews of public cloud infrastructure.
Checks such as mis-configured security groups, public EC2 instances can be done in a few simple steps at scale. All you would need is a lightweight compute instance and grant it read-only access to commonly used AWS services, Security Monkey would then iterate over your services and resources to flag potential security issues; web reports are generated for quick access and analysis.
This is what you can expect from a report out of Security Monkey:
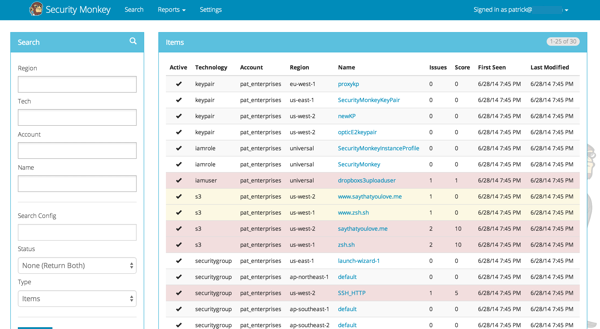
Source: https://e64-security-monkey.readthedocs.io/
Links :
#2 CloudMapper
Use Case : Cloud Network Visualisation & Configuration Scanning
Details : Provided as an open source project by DuoLabs, CloudMapper can be used to detect security issues as well as create visual network layouts of a public cloud deployment. The visualiser is a useful tool to map the extent of your public cloud network and potential integrations that could grant permissive access.
The security scanning module is quite extensive that actually saves the AWS configuration in well structured json files that can be used for future analysis. It also generates HTML reports for reviews. CloudMapper can be deployed in standalone machines as well as a neatly integrated ECS setup.
Here’s what a typical CloudMapper public cloud visualisation looks like:
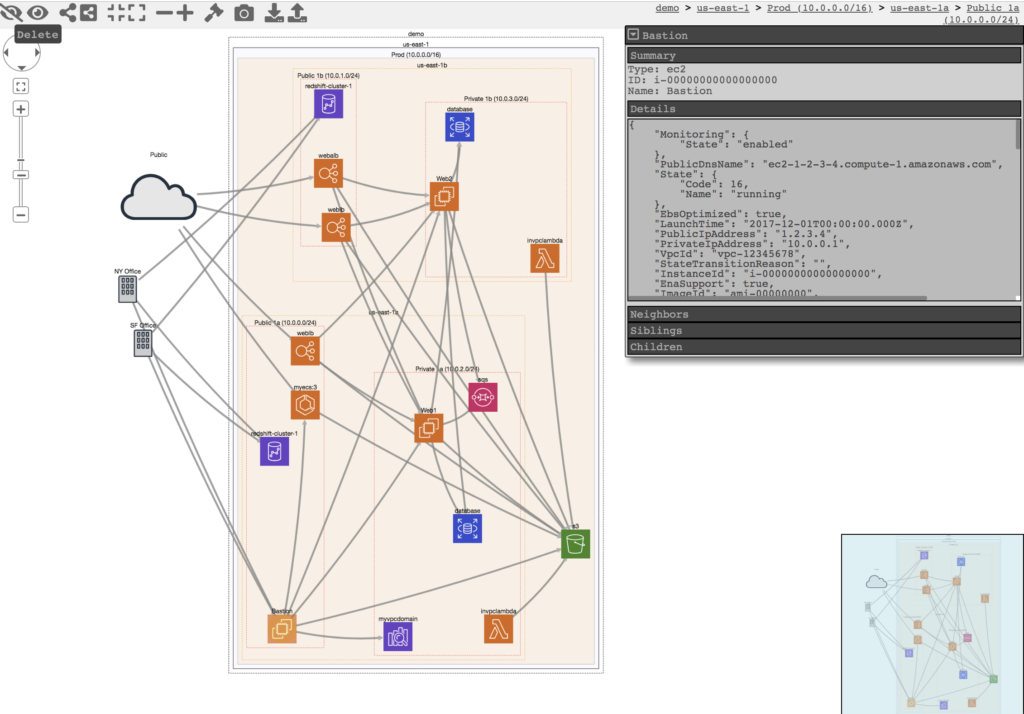
Source: https://github.com/duo-labs/cloudmapper
Links :
Identity & Access Management
A few picks from our end to manage identities and access at scale:
#3 Keycloak
#4 ConsoleMe
Use Case : Least Privileged Access Provisioning
Details : Yet another awesome utility by Netflix that helps organisations streamline their access provisioning process. Rather than relying on a trial and error approach, ConsoleMe enables engineering teams to request for cloud access using a workflow that ensures policies are created in an efficient manner and are minimum privilege. More no for AWS cloud deployments.
Links :
Github
Network Security
The first line of defence for an organisation’s critical network hosted assets! Here are a couple of enterprise grade network security tools that help protect your public facing assets.
#5 Snort
#6 ModSecurity
Data Security
You’ve probably heard this already – “data is the most valuable asset today”! So how does one go about protecting sensitive data, let’s look at few open source tools that help.
#7 Redash
Use Case : Database Wrapper
Details : At times, organisations need to grant database access to users for purposes such as analytics, investigations. In case direct access to the database is granted, it can lead to a variety of security issues since database users are usually native and not tied to individual user identities. Redash can be used as a wrapper on top of SQL databases as well as no-SQL databases to solve for this. It easily integrates with central authentication systems and provides role based access control.
Credential Security
#8 Hashicorp Vault
Use Case : Centralised Credential Storage
Details : A popular and enterprise grade credential vault that provides functionalities such as credential storage, encryption, rotation and API access. It eliminates the need to store credentials within code or local configurations hence minimising the risk of accidental credential leakage.
Links :
#9 Git-Secrets
Use Case : Credential Scanning
Details : Credentials get accidentally committed in a git repository, the git repository accidentally goes public, and there! Adversaries immediately have access to resources permitted by the secret. Git-secrets helps scan git repositories to discover credentials that might have been unintentionally left out there.
Vulnerability Management
Once you’ve nailed the public cloud control plane from a security standpoint, infrastructure comes next! And a comprehensive vulnerability management program is the starting point for infrastructure security.
#10 OpenVAS
Use Case : Detect Infrastructure Level Vulnerabilities
Details : One of the most popular open source vulnerability scanners available today! It provides discovery capabilities and ships with hundreds of vulnerability identification plugins.
While using OpenVAS, it’s best to integrate it with your CI/CD pipeline and invoke an OpenVAS API the moment a new infrastructure resource is spawned.
Threat Detection & Response
You’ve got some preventive security controls going, awesome! But a lot of organisations do, and they still get breached!
A famous quote by John Chambers (former CEO of Cisco Systems):
“There are two types of companies: those that have been hacked, and those who don’t know they have been hacked.”
What’s next?
Threat detection & response is the process by which an organisation enables itself to detect breaches or hacking attempts early on in the cyber attack kill chain. Thus hopefully stopping the adversaries before they’ve done too much damage or gotten hold of too much information.
Let’s talk about some open source tools that can enable such detection & response mechanisms.
#11 ElasticSearch, Logstash & Kibana
Use Case : Security Information & Event Management
Details : Needs little introduction, the ELK stack is an extremely fast and scalable log ingest and processing platform. It enables quick log ingest, parsing and enrichment post which indexed events can be analysed quickly via the Kibana interface. Security analysts can conduct investigations, or create dashboards to monitor security activity.
#12 OSSEC
Use Case : Host Intrusion Detection System & File Integrity Monitoring
Details : OSSEC is a popular host based intrusion detection system, which helps detect threats at a host level rather than a network level. It can be extended to respond to intrusions or threats via it’s Active Response component.
#13 Wazuh
Use Case : Security Information & Event Management
Details : Wazuh is a self sufficient threat detection platform that pulls inventory / host information and threat detection telemetry. This event stream is then collected and correlated centrally to alert on intrusions or threats.
#14 Ansible
Use Case : Security Orchestration
Details : Usually seen in the devops space, Ansible is primarily an automation and orchestration framework. IT or devops teams create Ansible playbooks to automate routine provisioning tasks; but that doesn’t mean it’s capabilities stop there. Security teams can leverage Ansible as a security orchestration platform in the incident response lifecycle to automate activities such as triage, remediation and containment. It ships with an array of integrations with most network or cloud infrastructure hence reducing the development overhead for such automation requirements.
#15 GRR
Use Case : Remote Forensics
Details : Google Rapid Response is a useful forensics tool that aims at simplifying remote triage, response and artifact collection. A python based GRR agent is deployed across endpoints and production systems, and a server interface is used to centrally run forensics tasks such remotely.
#16 Apache Metron
Use Case : Large Scale Security Analytics
Details : Initially termed as OpenSOC by Cisco, Apache Metron is a Hadoop backed security analytics platform. It is capable of ingesting a variety of log sources, carrying out realtime enrichment and streaming analytics.
Deep Packet Inspection
If going deep into threat detection & response is your thing, you’ve gotta try some deep packet inspection!
#17 Zeek
Use Case : Network Detection & Response
Details : Detecting the un-known should always remain a prominent aspect while managing an enterprise grade threat detection program. Most IDS/IPS or equivalent solutions run on signatures, which essentially means, it only catches threats that it is aware of (or has a signature for), the rest will fly under the radar.
This is where deep packet inspection (and of-course monitoring it) with tools such as Zeek helps catch those stealthy adversaries early in the kill-chain. The key here is to use deep packet inspection tools in conjunction with SIEM platforms to profile and flag un-usual network activity for the SOC team to investigate and action.
Summing up
There are hundreds of security tools out there, but finding ones that are tried and tested that solve for real problems might become a time consuming process. Hope this curated list of open source cloud security tools helps cut down that time on research. Apart from open source tools, there are cloud native services that provide alternate methods of achieving the similar objectives. In case you’re interested in reading further on this, check out our post around 7 AWS Networking Services Security Teams Should Know Of.
If you like what you read, sign up for our newsletter using the section on the left.

